Why should healthcare be afraid of ransomware? Here’s a quick roundup:
- Indian healthcare organisations witnessed a 37% increase in cyberattacks, with ransomware incidents showing the biggest increase
- The University of California, San Francisco, paid $ 1.4 million as ransom following a cyberattack on its School of Medicine
- Ransomware attacks on US healthcare organisations alone are estimated to have cost $20.8 billion in 2020
- Universal Health Services lost $67 million due to a ransomware attack and required 3 weeks to restore normal operations
- Hospitals that had been hit by ransomware and data breaches were found to have experienced 36 additional deaths per 10,000 heart attacks due to remediation measures
This list makes it clear that ransomware is not a threat that the healthcare sector can afford to ignore. The repeated and severe attacks against healthcare may create the impression that there is no solution to the ransomware scare – but that impression is wrong.
Which brings us to the good news: Healthcare organisations can deploy a range of measures to defeat ransomware.
Winning Against Ransomware
Before we begin discussing how we can win against ransomware, let us first address the belief that small organisations, or organisations that do not operate in large cities, will not suffer ransomware attacks because they are low value targets. This is not true.
Ransomware does not depend on your data having value to threat actors. It only depends on your data having value to you i.e., how well can your healthcare facility operate if you cannot access all or a majority of your data? Many enterprises will have to admit that they will not be able to operate at all, or will be able to operate with severely diminished capability. Additionally, your organisation may not be the intended victim of the attack but the attack can still spread to your organisation from another victim because we are all digitally interconnected in today’s world.
Quick summary: Your facility will be attacked if you are in healthcare, and the attack will most probably be ransomware.
With that out of the way, let us look at what your healthcare facility can do to defeat ransomware.
Anti-ransomware Measures
There are two types of anti-ransomware measures that you can implement to stop ransomware:
- Management/Organisational Initiatives – These include formulating a cybersecurity policy, maintaining password hygiene, and educating users against cyberattacks
- Technology Solutions – These involve using cybersecurity, like K7 Endpoint Security (K7 EPS), that is designed to detect and defeat ransomware
Our earlier blog Cyber-hygienic Healthcare – Preventing Digital Infections has a detailed discussion on the Management/Organisational initiatives that will need to be implemented. This blog will discuss the technology aspects of ransomware and how K7 Endpoint Security works to identify and block this cyberthreat.
How Ransomware Works
There are different flavours of ransomware but they all attempt to block your access to your data and devices, and demand a ransom to restore access. They block access by encrypting data. Some ransomware look for and encrypt files, such as Word or Excel documents, that are present on the device and some encrypt the Master Boot Record (MBR) to prevent the OS from loading.
How K7 Protects Against Ransomware
K7 EPS employs two methods to provide direct protection against ransomware:
- Signature-based Detection – The K7 Threat Lab analyses hundreds of thousands of malware samples every day and releases malware definition updates multiple times a day to identify ransomware by their signatures and stop them
- Behaviour-based Detection – Ransomware operators know that cybersecurity firms utilise signatures to stop ransomware, and develop obfuscation methods to hide their signatures. Behaviour-based detection uses heuristic scanning, monitoring potentially suspicious processes, and increases in file entropy to identify ransomware that is obfuscated. This method is also used to detect new ransomware that may not have a malware sample
One of the challenges faced in creating anti-ransomware solutions is the legitimate use of encryption for data security, which you may use in your organisation to protect private or proprietary information. K7 EPS is designed to differentiate between malicious encryption and legitimate encryption, and only stop the former.
Signature- and behaviour-based detection stops ransomware once the malicious payload is activated. K7 EPS also includes features that stop cyberthreats before their payload can be deployed, including automatic email scanning, blocking of phishing links and malicious websites, and scanning of USB drives (or even blocking them entirely if you wish) to stop malware ingress.
Speed Matters in Cybersecurity
The speed at which a cybersecurity solution can scan for malware is important in stopping malware before it can disrupt your operations, and K7 EPS is well known for its lightning fast scanning. But cybersecurity speed plays another critical role in healthcare protection.
This blog began with a list of bad news about ransomware which included an increase in fatalities caused by remediation measures rather than by the ransomware attack, because the remediation measures create delays, complications, and disruption. This cannot be an acceptable outcome for the healthcare sector.
K7 EPS is not just fast. It is also extremely efficient. AV-Comparatives of Austria discovered that K7 EPS had the least impact on device performance compared to other well known cybersecurity brands.
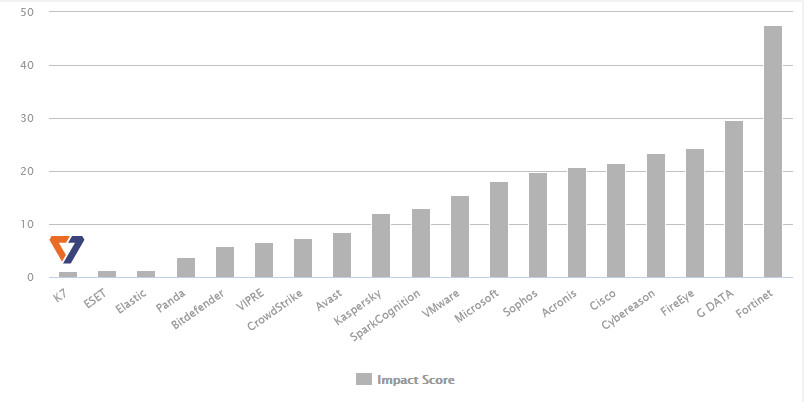
Source: AV-Comparatives
This means that K7 EPS does not slow down your endpoints and servers. Additionally, K7 EPS is engineered for lean updates i.e. the malware definition updates (which we referred to when discussing signature-based detection) are very small and do not choke networks. How small? K7 EPS has been successfully deployed in environments where connectivity is as low as 24kbps.
K7 EPS is also very easy to deploy and can be rolled out quickly across your facility (or facilities, if you operate in multiple locations) with minimal inconvenience. All these factors ensure that cybersecuring your organisation does not delay, complicate, or disrupt operations.
Ransomware is a dreadful digital infection, but it can be prevented. Please read K7’s whitepaper Unmasking Ransomware for more information on ransomware and K7’s anti-ransomware technology. Our whitepaper Accelerated Cybersecurity discusses how K7 emphasises speed in cybersecurity. Contact us to learn more about K7 Endpoint Security and why more than 70 healthcare organisations trust us to bolster their cyber defences against ransomware.











