Like what you're reading? Subscribe to our top stories.
Categories
Featured Posts
More Posts
 Android Blog Brute Force Attacks CISO Cybersecurity Enterprise Executive Insights Internal Attacks Internet Safety iPhone Leader's Guide to Cybersecurity Malware Obsolete OS Operating System Phishing Ransomware Social Engineering Tips Windows 7
Android Blog Brute Force Attacks CISO Cybersecurity Enterprise Executive Insights Internal Attacks Internet Safety iPhone Leader's Guide to Cybersecurity Malware Obsolete OS Operating System Phishing Ransomware Social Engineering Tips Windows 7
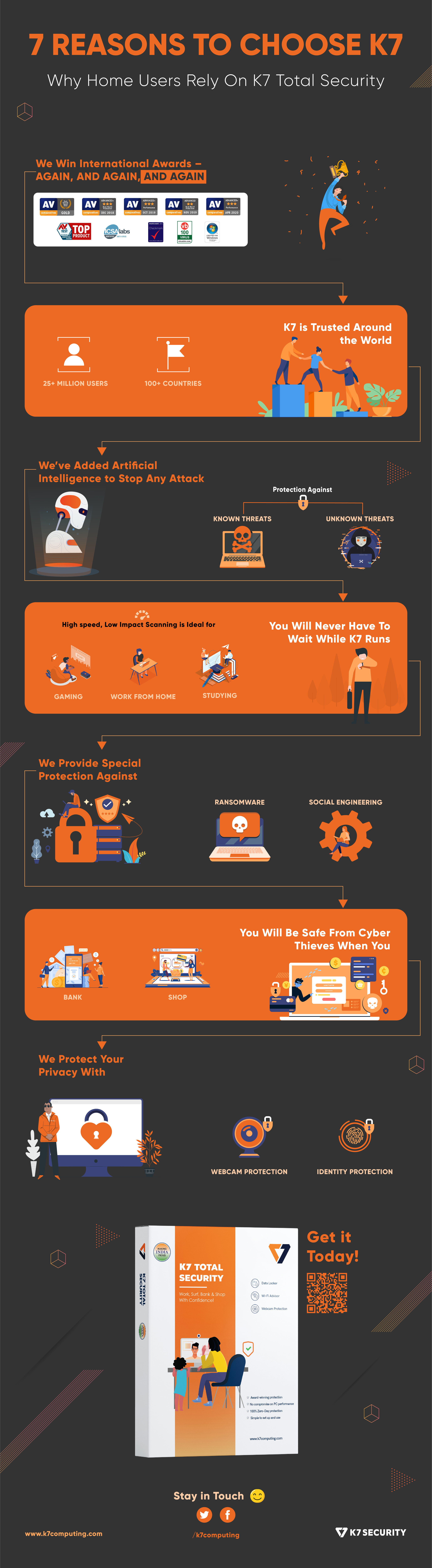
Shadow IT, the most significant cybersecurity risk during Covid-19, explained

Anirban RoySeptember 15, 2020
 Android Blog Brute Force Attacks CISO Cybersecurity Enterprise Executive Insights Internal Attacks Internet Safety iPhone Leader's Guide to Cybersecurity Malware Obsolete OS Operating System Phishing Ransomware Social Engineering Tips Windows 7
Android Blog Brute Force Attacks CISO Cybersecurity Enterprise Executive Insights Internal Attacks Internet Safety iPhone Leader's Guide to Cybersecurity Malware Obsolete OS Operating System Phishing Ransomware Social Engineering Tips Windows 7
Cyberattacks – What The BFSI Sector Should Know And Do

Raja Manuel MuthayyaMay 29, 2020








