Having your head in the clouds was once considered a bad thing, as was having a cloudy future. But digital technology now gives clouds a good reputation. Both our personal and professional computing requirements are rapidly transitioning to the cloud, and so is enterprise cybersecurity. Cloud Deployed Endpoint Security leverages the power of the cloud to give enterprise IT teams quick, convenient, and reliable control over enterprise IT assets.
What Cloud Deployed Endpoint Security Is and Isn’t
Let’s start with what it isn’t, first: Cloud Deployed Endpoint Security isn’t a solution to secure applications that run in the cloud. It is a solution that uses the cloud to manage the cybersecurity of enterprise endpoints and servers.
Why Should Endpoint Cybersecurity Be Managed From The Cloud?
Before wireless internet became available almost everywhere, office work only happened in the office and the IT perimeter was clearly defined as were the hours of work. That world no longer exists for many of us. The modern enterprise is boundaryless: employees do work in the office but they also work at home, in coffee shops, and in planes, trains, and automobiles. They also work at any hour of night or day because modern business is a 24/7/365 responsibility. The sun never sets on the globalised enterprise; there is always a customer facing peak workload somewhere in the world, and we need to be always ready to respond to them.
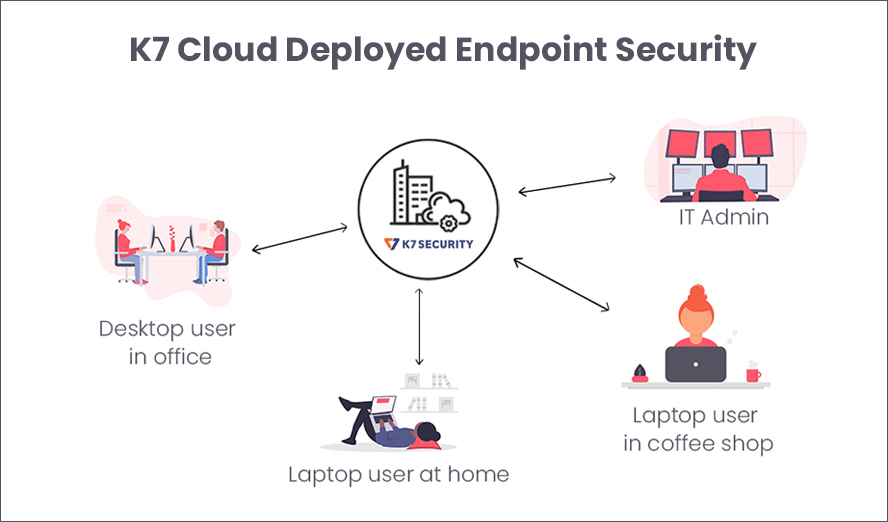
Enterprise cybersecurity has to march in step with how the enterprise functions. When an employee may be at work at any time from anywhere, then they, and by extension the organisation, are vulnerable to cyberattack at any time and wherever they are. Cybersecurity teams have to be equally equipped to monitory enterprise cybersecurity at any time, from anywhere – and that’s where the cloud comes in.
Old vs. New: The Differences Between On-Premises and Cloud Deployed Endpoint Security
On-premises Endpoint Security – At a Disadvantage in a Changing World
The traditional cybersecurity model had the endpoint security console installed on a machine in the facility. All endpoints were located within the same facility and connected to the console using the enterprise network. To manage enterprise cybersecurity, the IT team had to be physically present in the office to access the console – which is fine, as long as all endpoints are also physically present in the office and only connect using the enterprise network.
This system does have its advantages: the IT environment is highly predictable and easy to lockdown, and is therefore easy to control and secure. It has only one disadvantage, but it is a significant one: it does not adapt to endpoints leaving the IT perimeter when they leave the enterprise premises.
This disadvantage is significant because employees increasingly work from outside the secure IT perimeter, but they are still accessing business networks and data. This makes the enterprise highly vulnerable to a cyberattack!
Cloud Deployed Endpoint Security – The Advantage That Is Essential For Modern Business
This new cybersecurity model moves the console from the premises to the cloud. Each endpoint connects to the cloud console directly through the internet. This means
- Anytime, Anywhere Control – Enterprise cybersecurity is no longer constrained by time or place. All it takes is a browser and an internet connection to log into the console and manage enterprise cybersecurity across all endpoints, no matter where are. All policy changes are automatically synced between the cloud and endpoints as soon as they come online. Definition updates also flow directly from the cloud to each endpoint
Along with this, there are several other advantages which increase the value proposition of Cloud Deployed Endpoint Security:
- No local server maintenance – Since the cloud deployed solution does not require a local on-premises server, the business avoids the need to maintain that server and take a backup of the cybersecurity solution’s database. These are handled by the vendor in the cloud
- No installation of updates – Any feature upgrades to the console are rolled out to the cloud console by the vendor and are immediately available to the business. There is no need to spend time on updating the console, or worry about any glitches that might arise due to how specific local hardware and software combinations might interact with the updated console
- 100% Remote Installation – Since the console is in the cloud, the vendor’s team need not visit business facilities to install any software. Similarly, the direct link between the endpoint and the console avoids the need to bring the endpoint to the business office for installation of any software; the endpoint installation can be delivered through a link sent to the endpoint for direct installation
- Rapid Deployment – Endpoint protection can be rapidly deployed across the organisation as IT team capacity no longer determines the speed of the cybersecurity rollout
Who Should Choose Cloud Deployed Endpoint Security?
The pandemic has shown us that any organisation, and every organisation, will need to be ready to transition to remote working overnight, and the security offered by the traditional IT perimeter can become insufficient under such circumstances. Therefore, every enterprise needs to consider transitioning to cloud deployed endpoint security which can adapt to changing business realities.
K7 Security’s Cloud Deployed Endpoint Security protects our enterprise clients from a wide variety of cyberthreats and helps them achieve operational flexibility by being as boundaryless as their business. Try Cloud Deployed Endpoint Security or Contact us to learn more about how we can help future proof your enterprise cybersecurity.











