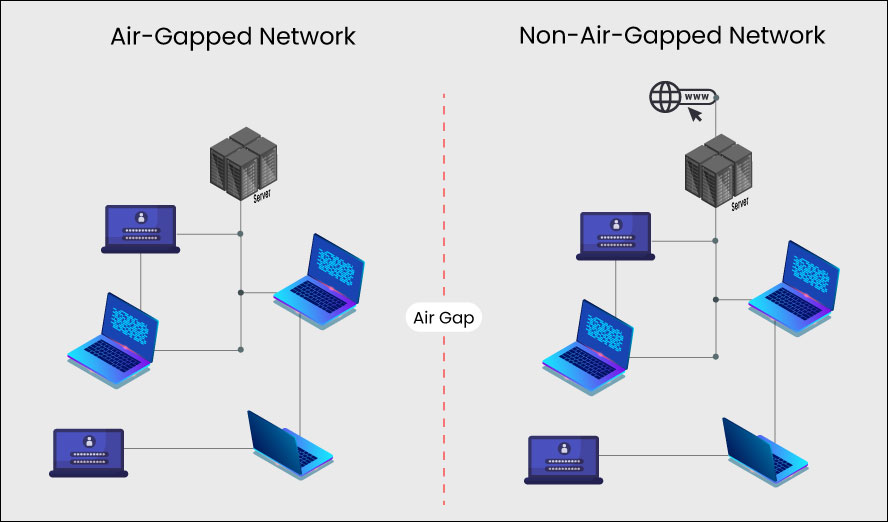
What is an air gapped computer or network? Air gap means physical isolation i.e., the device or network is physically separated from other devices or networks. It is regarded as the ultimate cyber defence strategy for those who absolutely cannot afford a cyberattack or risk malware infection because the device or network is physically isolated from the outside world. Think of it as social distancing to stop computer viruses.
Why Does Anyone Need An Air Gapped System?
Air gapped systems are typically required in IT ecosystems which manage critical infrastructure that must never fail, or which store confidential information that must never be leaked. There are a few niche cases as well, where they are used by researchers or enthusiasts.
Typical Use Cases
- Critical Infrastructure
- Power Plants
- Medical Equipment
- Industrial Equipment
- Confidential/Critical Information
- R&D Centres
- Cryptocurrency Wallets
- Defence Networks
Niche Cases
- Obsolete OS/device
- Malware Infected Device
Niche cases, such as needing to view information contained in a malware infected device or a device with a highly vulnerable obsolete OS, are unlikely to expand much.
The typical uses cases, however, are likely to expand as connected devices/Internet of Things become ubiquitous. 10 years ago we may have never needed to wonder if a light switch in a factory needs to be air gapped, but the question is becoming increasingly relevant now when we not only have smart switches but even smart light sockets. Commercial and industrial establishments may prefer to air gap any system that doesn’t need to be connected, directly or indirectly, to a network linked to the outside world.
How Can A System Be Air Gapped?
Despite the term ‘air gap’ only requiring a physical gap through which air can pass, the term has to be interpreted metaphorically in today’s world where devices and networks can connect wirelessly with ease. What constitutes an air gapped system may depend on its purpose, but it will usually require:
- No Wired Network Access – To ensure that network access is removed, wired network access may be disabled through software or the networking hardware may even be physically removed for maximum security
- No Wireless Network Access – Wi-Fi, Bluetooth, Near Field Communication, Infrared Communication, and any other wireless data transfer method will need to be disabled at least through software, and the hardware may need to be physically removed or disabled to prevent the possibility of malware reversing the software block
- No Removable Storage Device Access – USB drives can be disabled to prevent someone with physical access to the device from inadvertently or intentionally introducing malware into the system. As the device is not connected to a network, re-enabling such access (if required) has to be performed manually with direct physical access to the device
- Restricted Physical Access – Access to the device/network itself should be physically restricted. Who can access, when they can access, who should authorise such access, who should supervise such access should be decided and formalised as a security policy to be strictly followed
- Restricted Use of Other Devices – Air gapping may fail to secure the system if a user can photograph data on the device screen with their mobile phone. Devices that can capture and transmit data may need to be banned near air gapped systems
- Clean Installation – A clean installation of the operating system and necessary applications may be required to eliminate malware that may have already infected the device
- Physical Security – All these precautions will not be effective if someone can steal the device itself. Physically securing the device may be required if the device is portable and the data it holds is very valuable
Are Air Gapped Systems Completely Safe?
Air gapped systems may need to either receive or export data. For example, critical infrastructure may need firmware updates and R&D centres may need to backup the intellectual property they develop. Data may need to be transferred through USB drives, and this raise the possibility of vulnerabilities.
The Stuxnet worm is designed to penetrate air-gapped systems and reportedly damaged Iran’s nuclear programme. Other exploits that can jump air gaps have been demonstrated. These are extremely sophisticated attacks that are quite difficult to accomplish, but they are technically possible.
Is There An Alternative To Air Gapping Systems?
There is a reason why we have networked devices and networks that connect to the outside world: networking radically transforms information sharing and thereby improves efficiency, collaboration, time-to-market, innovation, and so many other good things that make today’s world possible and shape the world of tomorrow.
The vast majority of businesses need a cybersafe way to conduct commercial operations. K7 Security’s Endpoint Security protects enterprise IT environments and allows businesses to serve their customers without fear of attacks from cybercriminals. Contact Us to learn more about our enterprise cybersecurity solutions that are used to protect highly secure facilities without the inconvenience of air gapping.











