Much has been spoken and written about how the pandemic has transformed business operations. This transformation has involved a cultural transformation, of achieving communication, collaboration, and accountability without meeting in person, and a digital transformation, as this change in culture has been possible only because digital technologies and connectivity have enabled various forms of remote working.
This transformation has not been limited to large, multinational corporations. All businesses, from neighbourhood stores to large enterprise, have been faced with a transform-or-perish choice. Micro, Small, and Medium Enterprises (MSMEs) have had to rush into digital transformation to maintain business operations and continue to serve customers, but have previously lacked the resources and knowhow to ensure secure digital transformation. Two years into the pandemic, MSMEs are now comfortable with digitally-enabled operations and are turning their attention to cybersecurity – which is now required by MSMEs more than ever.
Why MSMEs Are Targeted By Cyberattackers
MSMEs may have previously considered themselves too small to interest threat actors, but that no longer holds true for 3 reasons:
Evolution of Cyberthreat Ecosystem
Cyberattackers have borrowed from the legitimate software industry and embraced Software-as-a-Service (SaaS), now offering Ransomware-as-a-Service (RaaS) where attack developers license their attacks to others with limited skills and experience. This makes MSMEs viable targets for the licensee attacker who prefers to extract ransom from smaller organisations.
Change in Attackers’ Priorities
The Colonial Pipeline attack in the USA was a tipping point for the cyberthreat sector as it elevated ransomware attacks from corporate headache to national security threat. Many cyberattackers do not wish to invite the attention of security and intelligence agencies and are therefore moving from big game hunting to smaller targets like MSMEs.
Poor MSME Cybersecurity
Many MSMEs have implemented digital solutions without the safeguards that large enterprises usually have, making MSMEs easier targets for cyberattackers.
While the first 2 points listed above are beyond the control of MSMEs, the last point, regarding poor cybersecurity, can and should be addressed to prevent devastating cyberattacks.
Where MSMEs are Most Vulnerable to Cyberattacks
We can understand where MSMEs are most vulnerable to cyberattacks by analysing the critical areas where organisations have implemented or enabled digital transformation, and the associated cyber risk:
- Remote Working – Working from home has been the most obvious facet of digital transformation, and brings risk in the form of inadequately secured devices provided to employees in the rush to implement remote working, and employees accessing corporate IT assets through their personal network (home broadband or even mobile hotspot)
- Remote Access – Many organisations use Remote Desktop Protocol (RDP) to enable remote access to on-site computing resources for employees working from home. Inadequately secured RDP deployments provide opportunities for threat actors to compromise corporate IT ecosystems
- Digital Teamwork – Meeting KRAs is a priority for all businesses and many organisations have been forced to allow teams to use the solution that works best for them to ensure that targets are met. This not only results in solution fragmentation, with different teams using different applications (both on-device and cloud-based) to perform the same task resulting in the creation of silos, but also leads to the growth of Shadow IT when teams use unauthorised applications that have not been vetted for security or data sovereignty compliance
- Legacy IT – Older, unsupported IT assets that were previously used within the confines of the organisation’s IT perimeter have now been exposed to the public internet to facilitate remote access, leading to increased cyberthreats from unpatched vulnerabilities and insecure access
- Social Media – Businesses have switched to using social media as their primary method of accessing new customers and renewing bonds with current and past customers. Increased social media participation has increased risk of cyberattacks that originate on social media
- Tech-enabled Workforce – All employees have been tech-enabled overnight – but not all employees are digital natives or even familiar with digital ecosystems. This unfamiliarity makes them vulnerable to attacks that target the user rather than the device
How MSMEs can Improve Cybersecurity
With the above analysis of cyber risk in MSMEs that have pursued digital transformation, it becomes easy to frame measures that MSMEs should adopt to improve organisational cybersecurity:
- Create a Cybersecurity Policy – A cybersecurity policy is a document that lays downs the organisation’s standards for cybersecurity, and acts as a point-of-reference that ensures all employees understand their roles and responsibilities in the context of cybersecurity including accepted use of official social media. The policy should also stipulate penalties for non-compliance
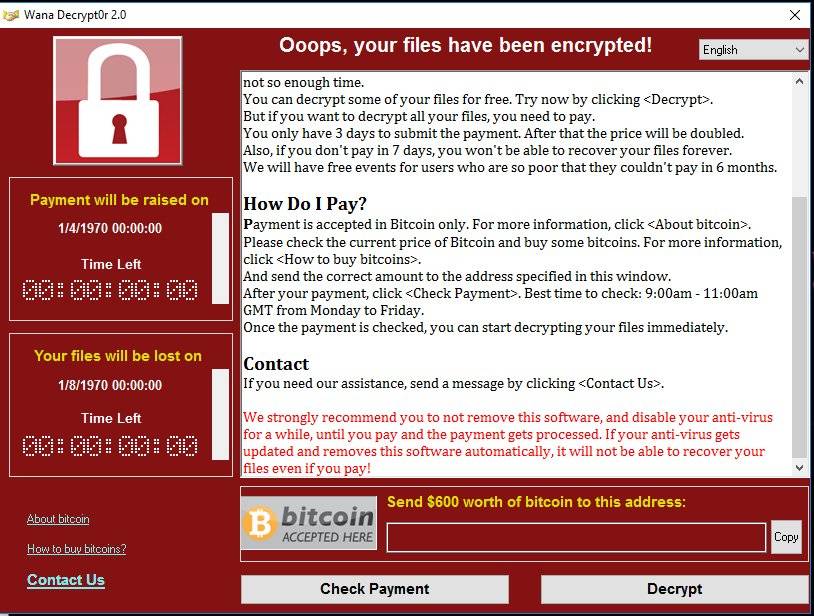
- Update & Patch – All updates and patches released for devices and applications should be applied as soon as they become available. The WannaCry ransomware was able to spread across the world because many computers had not been updated despite Microsoft releasing a patch for the vulnerability
- Secure Remote Access – Remote access through RDP can be secured by following best practices such as not using default ports, and revoking remote access as soon as it is no longer required. Remote access to the Tally server can be secured by using K7 Tally on WAN
- Deploy Endpoint Security – Enterprise endpoints (desktops and laptops) can be secured wherever they are locating using a security solution like K7 Cloud Endpoint Security which supports 100% remote deployment and management. Employees working from home will not need to bring their already issued devices to headquarters to gain protection
- Endpoint security can also be used to eliminate Shadow IT by controlling which applications can be used and which cloud services can be accessed
- MSMEs using G Suite/Google Workspace can use G Suite segmentation in K7 Cloud Endpoint Security to limit access to G Suite accounts linked to the organisation’s domain, preventing access to both personal Gmail accounts and G Suite accounts linked to other domains
- Deploy Network Security – Gateway security, such as K7 Unified Threat Management devices, can be used to protect the network of a business, creating a secure perimeter within which IT assets can be used safely. Authentication, Authorisation, and Accounting (AAA) framework enables intelligent access control to IT resources
- Upgrade Legacy IT – Any device or application that is no longer supported by the vendor should be upgraded to a currently supported solution. If using legacy IT is unavoidable, such solutions should only be used if they are protected by endpoint and network security
- Provide Cybersecurity Training – A well informed workforce is the organisation’s best defence against social engineering attacks like phishing that can target employees through email, phone, SMS, WhatsApp and social media, on both their professional and personal devices. Cybersecurity training programmes help employees to identify such threats, practise cyber hygiene, and implement measures to secure their personal networks
K7 Security’s international award winning solutions provide robust, multi-layered cybersecurity for businesses of all sizes. Contact Us for more information on how we can help you secure your organisation and your team against cyberthreats.