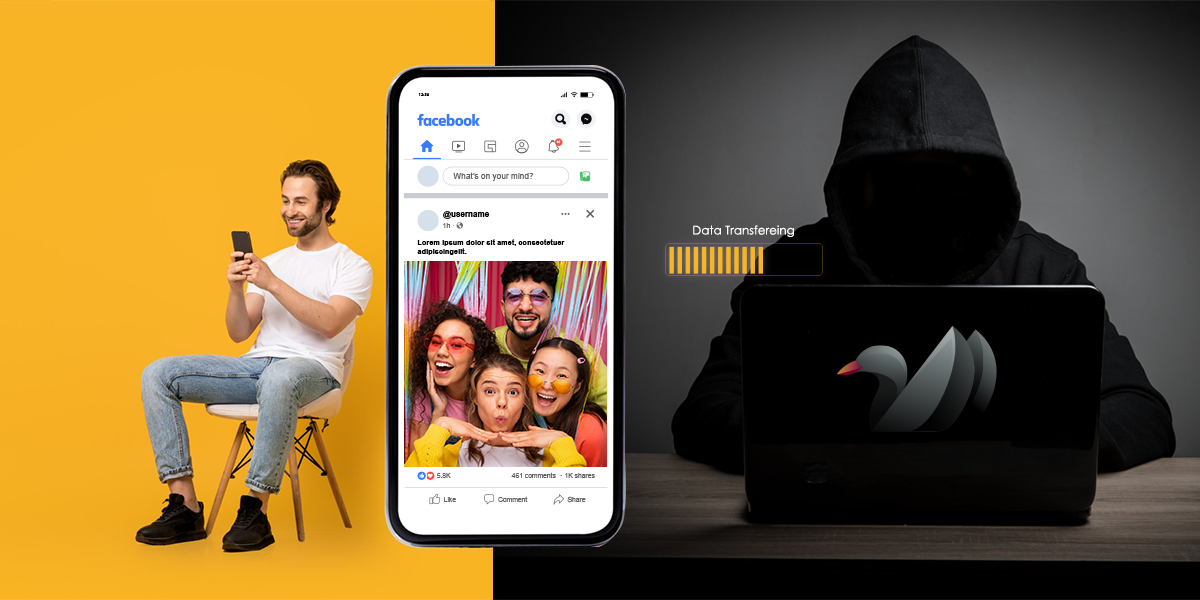
Ducktail is an info-stealer malware with its primary focus on stealing data related to Facebook. This group primarily relies on social engineering tricks to lure victims to download and execute the payload. They make use of Disk Image files like ISO, and ZIP files, to deliver their initial trigger.
Analysis:
In our case, the victim is lured to download a ZIP file disguising itself to be a job description. On double clicking, the user is presented with these files seen below.
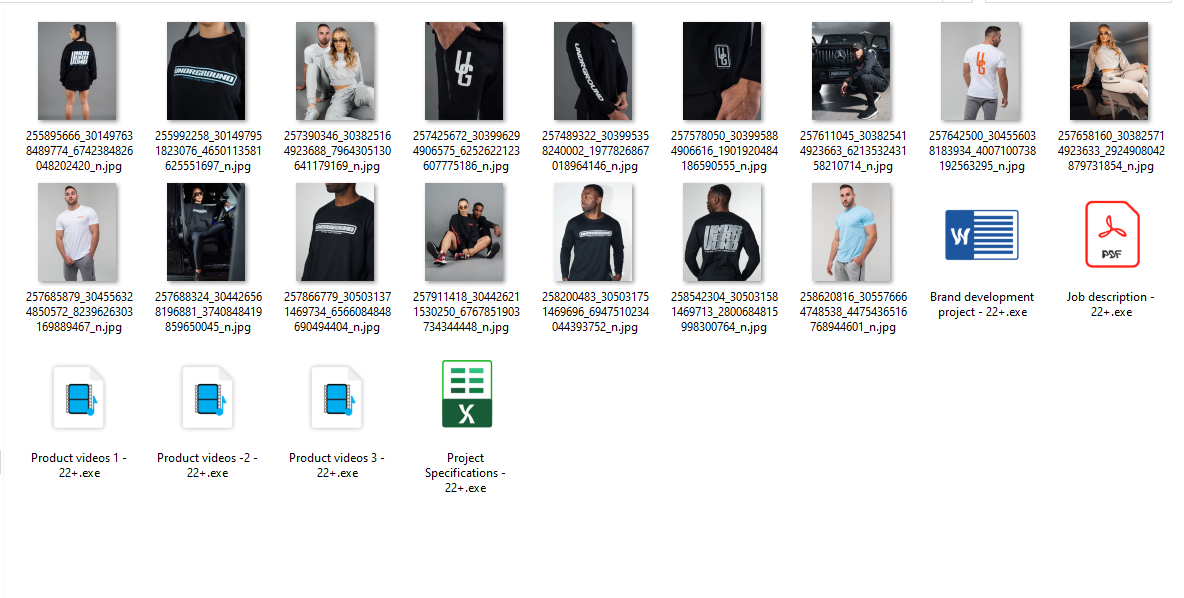
Figure 1: Files inside ZIP
There are 6 ducktail stealers embedded within this ZIP payload. We can see from the image above, the usage of social engineering involved in naming the executable file, as the icon of the executable is replaced to imitate a PDF/Excel file. All the executables have proper digital signature with validity so as to evade AV detection/Hooks.
Since the payloads are compiled using a single file feature present in .NET core, all the dependencies which are needed are packed together to make the file larger.
On Execution, all the dependencies for .net are dropped in the temp folder along with the main malware.
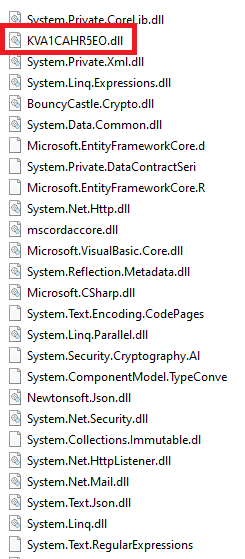
Figure 2: Contents of Ducktail Package
The malware is a 64bit DLL file, which is invoked automatically after all the dependencies are dropped. On execution, the malware(stealer) starts to collect all the cookies present in different browsers and sends it to C2(Telegram Link). It uses the collected Facebook login cookie to add new power users and generate a huge paycheck for the victim.
Mitigation:
Terminate all the browser sessions and immediately change the password for all accounts to a strong password. Always follow best practices while surfing the internet. Periodically change password used, and re-verify the users who are in the business account group.
The DuckTail Malware variants will be detected as “Trojan ( 0001140e1 )” by K7
Users need to be cautious and skeptical before clicking on any such ads so that they do not become a victim of such frauds. Users are requested to install a reputable security product such as “K7 Total Security” and keep it updated to stay protected from such threats.