This blog is about how Microsoft has done their bit to make working on office documents a tad safer for users. You want to know how? Well, they have blocked the execution of macros from documents freshly downloaded from the Internet, by default. Before we go to the WHY of it, let us understand what macros are being used for?
Need for Macros
As per Microsoft, macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically.
To sum it up, macros have made life easier by automating repeated tasks, so as to save time on keystrokes and mouse actions, for those who extensively use Microsoft office.
So with this new policy in place, does it mean users won’t be able to use macros anymore? Of course not!. Macros can be manually enabled if you really trust the sender and are sure it is not malicious, albeit at your own risk.
Why did Microsoft implement this new policy?
Threat actors have always tried to abuse any technology that comes up. Macros are one of their favourites when it comes to the initial attack vector. Threat actors embed macro based attachments or downloadable links into seemingly unsuspecting emails, and use social engineering tactics to lure users into opening the email and make the user execute the malicious payload by enabling macros. Though this is the most common way, it is just one among other ways in which macros can be abused. Few of the other ways are spreading them via downloadable links or by abusing a cloud service. Since all this is being done using a Microsoft feature, AV vendors find it difficult to properly distinguish between legitimate usage and malicious usage.
How is Microsoft doing it?
Tagging files with the Mark-of-the-Web (MOTW), which indicates that a file is fresh off the Internet. When a file is tagged as MOTW, that file should be treated with suspicion and in case of a MSOffice file containing a macro, the user will not be given easy default access to execute the macro.
How are threat actors reacting to it?
They have already started using file compressions like zip,7zip, etc in the form of a wrapper or container so that the MOTW tag will be applied on the outer Zip file only and the inner malicious file will be uncompressed and run without MOTW hindrance. Other such container file types include ISO,IMG, etc.
Many researchers have assessed the MOTW implementation and have already enumerated possible methods in which MOTW could be bypassed to execute freshly downloaded malware as shown in this tweet.
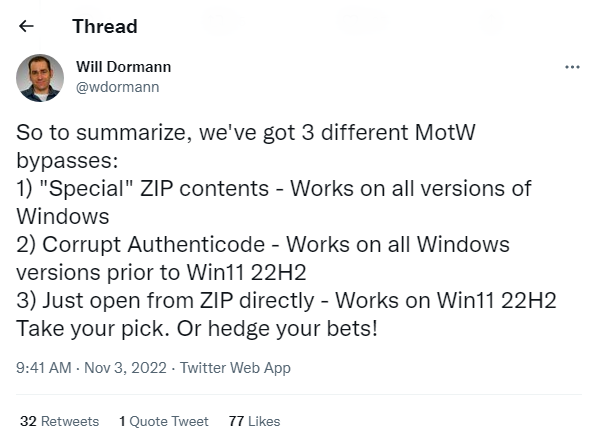
Figure 1: Tweet showing MOTW bypass techniques
Conclusion
Users must perform the basic defensive technique of steering clear of downloading and executing files from unknown sources and reporting any suspicious emails to the concerned authorities. Organizations should train and update users on a regular basis regarding the latest threats and social engineering tricks. Apart from all these, AV vendors should focus more on a layered detection approach to safeguard its customers.