Hunting threats online on a daily basis is a tough task, and our researchers at K7 are embracing challenges and excelling while finding out emerging loopholes everyday. The bunch of researchers (we call them cyber ninjas) at K7 Computing combat bad guys every day from taking down our users’ network or reigning over the internet.
Recently one researcher from the K7 arsenal dubbed Dinesh Devadoss has chased down a new species of fileless malware targeted to MacOS users. Developed by the infamous North Korean Hacking Group Lazarus APT, the malware is loosely based on AppleJeus and camouflage as a crypto trading software to infect the victims’ machine.
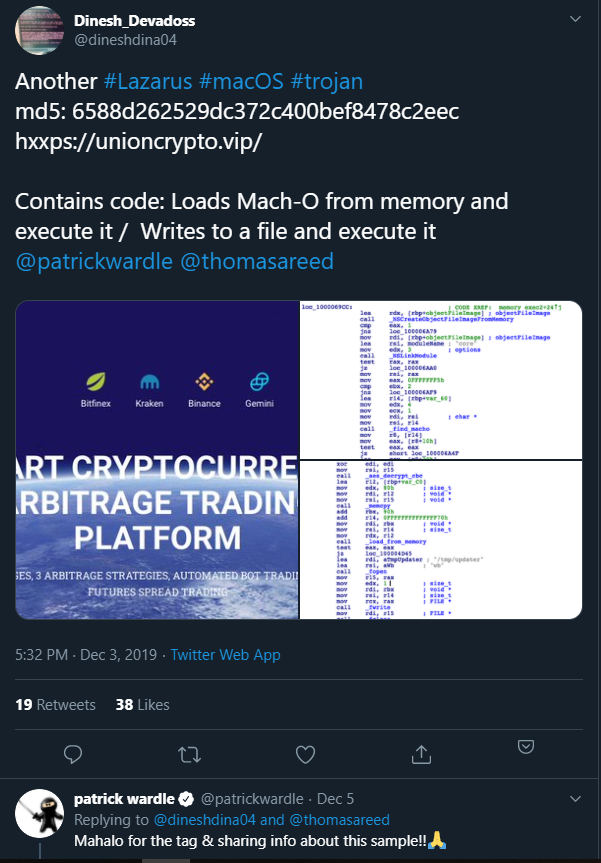
In short, the attack begins with a social engineering trick asking potential victims’ to install a cryptocurrency app, which is fake, on your macOS powered device.
Once the victim installs the app, it downloads the first payload carrying the Trojan inside and infects the device.
The Trojan downloads the second stage payload on a later stage which remains active in the system RAM of the device and doesn’t install anything on the device.
The Trojan also injects an executable file into the bootloading process of the device to remain undetected.
Cybersecurity research service Virustotal has listed 19 out of 70 anti-virus suites are capable of detecting the threat as malicious, and two K7 products count in the list.
Curious to know more? Read more about the detailed analysis of the Trojan’s kill Chain by Dinesh here.











