Phishing is a type of social engineering attack method wherein threat actors send phony emails to users, tricking them into revealing their sensitive information or for deploying malware on their devices. Phishing has always been an easy and convincing lure for threat actors to trap victims mainly because, however well-trained the users are, threat actors go a step ahead in writing very credible fake emails.
Why do people keep falling for this bait?
The one simple reason is the human factor involved. Even though organizations train their users regularly and raise awareness about the latest phishing techniques, sophisticated threat actors do create such convincing emails and use innovative social engineering tricks to find their next victim, who could be, who knows, the one who was trained to be safe. The only trickiest part for the threat actor(s) is to convince their prospective victim(s) to respond immediately to the call to action (CTA). If they do, the bait laid was a success.
Recently, one of my colleagues received an email, purportedly from a Barrister, saying a personal message has been sent in the attachment, as shown in Figure 1.
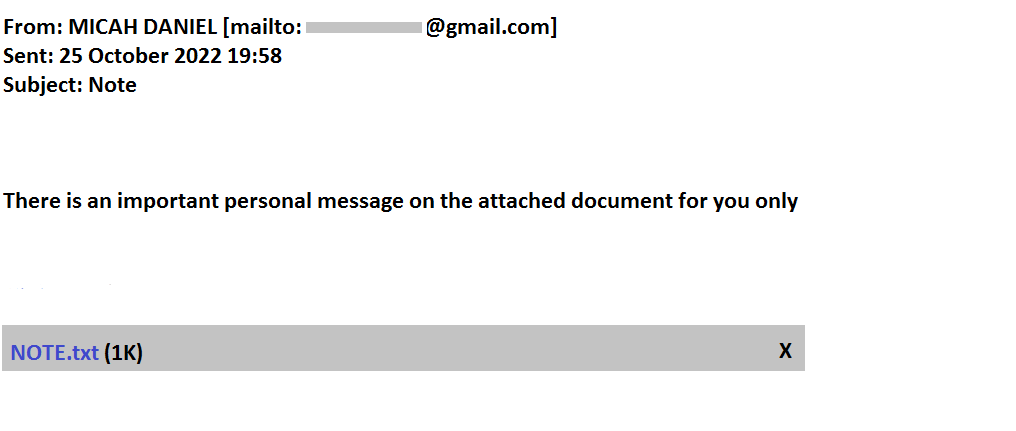
Figure 1: Phishing email received
Figure 2 shows the content in the “NOTE.txt” attachment.
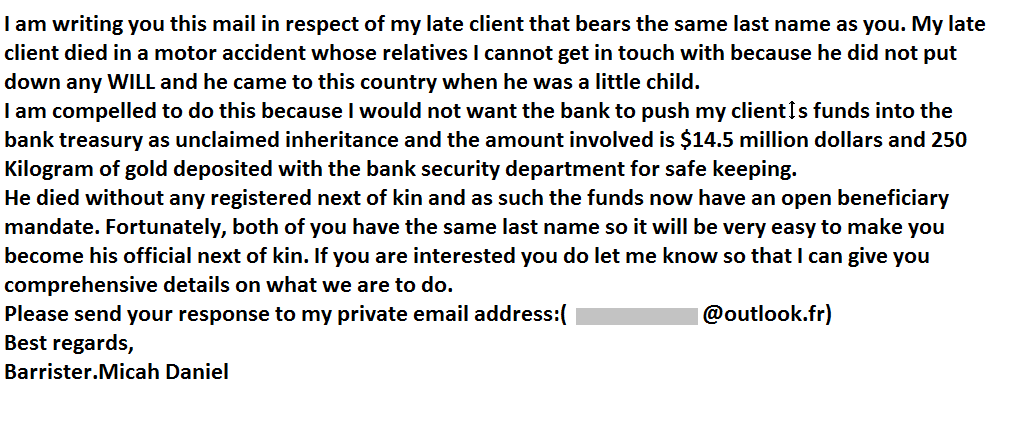
Figure 2: NOTE.txt, Suspicious Attachment
When our colleague reported this to us, we decided to blog about this, primarily to raise awareness about such ruses. So, let us now understand why we classify this as a suspicious email and how we are saying that the email is not from an authentic source.
The Email Anatomy
Let us now analyse the message header, body, and signature separately.
Message Header
- Email is from a public domain (here, gmail.com) instead of a specific domain where the concerned person is affiliated with
- The subject of the email is not specific to the topic that is being discussed (here, Note)
Message Body
- Grammatical and sentence structuring errors, not definitely from someone at the rank of a Barrister
- Sense of greed and urgency and a lure (The huge amount involved)
- Asking to reply to his private email address is suspicious. The email is sent from Gmail, and a reply is requested in Microsoft Outlook, and both are to his personal email ids
- The client’s country of residence has not been mentioned anywhere in the email
- The last name of the client has not been revealed
- The attachment name NOTE.txt is too generic and not specific to the email of concern
Message Signature
- No Barrister of reputation will transfer ownership to someone with the same last name
- Any Barrister knows the amount is in safe custody with the bank as long as the legal heir comes to claim and will never transfer those to some random person with the same last name as their client’s
Our analysis leads us to conclude that this is a phishing attack and that users should not become victims of such emails so that they don’t lose money or have malware installed on their devices. Even though this email does not have any malicious executables embedded in it, if the user proceeds with the email conversation, threat actors might ask the user to enter bank details and other info on a malicious link shared by them and this could install malware on their device and possibly keyloggers too, logging all your keystrokes which would then be sent to the threat actor(s) for misuse.
Why are threat actors so successful at Phishing?
Phishing has become a household name these days, at least among the cyber community. As a result, users feel it is very easy to identify a phishing email. But considering how threat actors use sophisticated techniques such as Business Email Compromise (BEC) attacks, among other convincing social engineering lures, making even a well-trained user susceptible. It has come to a point such that it is very difficult to differentiate between the original and the fake. There is a very thin line between them, and only a few escape from being trapped.
Takeaways
Users are requested to refrain from replying to any email they find suspicious or not convincing and report such scenarios to the concerned authorities. Users are advised not to click on unknown links or attachments from suspicious sources. The organization needs to impart phishing awareness training to their employees, customers and vendors so as to safeguard its network and devices. Organizations should also warn their employees, customers and vendors of BEC attacks and to not respond or take action on any email they have an iota of doubt regarding its legitimacy and report the same to the organization. Be Warned and Stay Safe!