Cybersecurity is receiving a great deal of emphasis in boardrooms due to the destructive potential of cyberattacks, but the emphasis is accompanied by uncertainty – where should attention be directed? Digital infrastructure in modern organisations is very complex which is further compounded by operations that are distributed across regions, requiring compliance with multiple regulatory requirements. Maintaining cybersecurity in this environment becomes much easier when businesses have a list of the digital assets that are most likely to be attacked or vulnerable areas that are most likely to be targeted. The OWASP Top 10 provides this list.
What is OWASP?
The Open Worldwide Application Security Project (OWASP) is a community of volunteers who promote the development and acquisition of trustable and trusted applications and APIs. The resources provided by OWASP are free and open to access by anyone. OWASP is a non-profit foundation that has over 250 local chapters worldwide with tens of thousands of members, and is not affiliated with any technology vendor.
What is the OWASP Top 10?
The OWASP Top 10 is a list of the 10 most critical security risks to web applications arrived at by gathering data from a variety of sources. Software developers and cybersecurity professionals can use the OWASP Top 10 to prioritise their efforts towards mitigating the risks that are most likely to be faced by applications and APIs.
The latest version is OWASP Top Ten 2025, which we will examine in this blog.
OWASP Top 10 2025
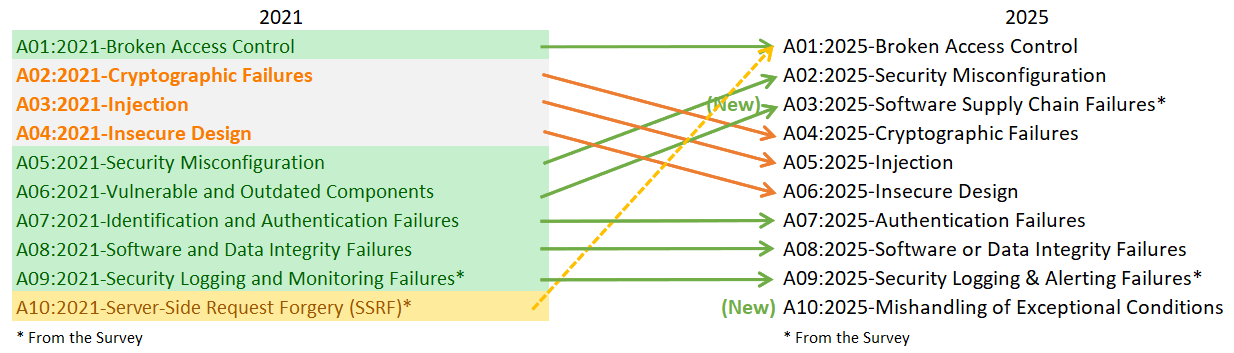
Changes from the previous version (OWASP Top 10 2021) to OWASP Top 10 2025 are summarised below:
Source: owasp.org
The comparison table reveals 2 new items (Software Supply Chain Failures, Mishandling of Exceptional Conditions) that have been added to the 2025 list, though Software Supply Chain Failures is an expansion of Vulnerable and Outdated Components from 2021. Server-Side Request Forgery has been included under Broken Access Control. Other items have been reprioritised or have retained their ranking from the 2021 list. We will discuss each of the list items in detail.
1. Broken Access Control
Broken Access Control refers to a user (human or machine) gaining unauthorised access to resources e.g., a user may be able to login and then access another user’s data. This vulnerability was top ranked in OWASP Top 10 2021 and retains that rank in OWASP Top 10 2025. As previously mentioned, Server-Side Request Forgery, which was independently listed in OWASP Top 10 2021, is now included under Broken Access Control in OWASP Top 10 2025. K7’s detailed examination of Broken Access Control is found here.
2. Security Misconfiguration
Security Misconfiguration is a vulnerability that occurs when any digital asset (device, software, cloud service) has not been configured correctly in terms of security even if the configuration supports required business functionality. These include use of default passwords, users having unnecessary elevated privileges, unlimited login attempts, and firewall policies permitting any-to-any traffic. Security Misconfiguration was ranked #5 in OWASP Top 10 2021 but has now increased in criticality and has been ranked #2 in OWASP Top 10 2025.
3. Software Supply Chain Failures
The Vulnerable and Outdated Components vulnerability occupied rank 6 in OWASP Top 10 2021. This category has been expanded to include all vulnerabilities in the software supply chain and is ranked #3 in OWASP Top 10 2025. A software supply chain failure is a vulnerability in a software that is used by the enterprise (supplied by a 3rd party) or a vulnerability in a software component that is used to develop enterprise software. It should be noted that a software (or digital) supply chain failure is distinct from a conventional supply chain attack where an organisation is compromised by first attacking a vendor.
4. Cryptographic Failures
Cryptographic Failures are vulnerabilities related to encryption of data at rest and in transit, either through lack of encryption (e.g., using HTTP instead of HTTPS to transmit credentials) or through the use of encryption methods that can be defeated (e.g., MD5, SHA-1). Robust encryption ensures that, even if a cyberattack is successful, exfiltrated data will be useless to the attacker while weak encryption creates a false sense of security.
5. Injection
Injection is the insertion of malicious code into otherwise benign input. SQL Injection (SQLi) is incorporated into database queries to trick the database server into performing unintended actions. Cross-Site Scripting (XSS) is the insertion of malicious code into benign websites through non-validated user input. K7’s detailed examination of SQL Injection and Cross-Site Scripting is found here.
6. Insecure Design
Insecure Design refers to software that has security flaws in its design or architecture e.g., having default credentials that are easy to guess or having elevated privileges for all users. Adding cybersecurity as a layer over insecure design will not usually be sufficient mitigation, and such flaws can be fixed or avoided by developers by following Secure By Design principles.
7. Authentication Failures
Authentication mechanisms ensure that only authorised users are allowed to access business systems with authorised access privileges. An Authentication Failure may allow an unauthorised user to access business systems e.g., unlimited login attempts permit brute force attacks. K7’s examination of Authentication Failure is found here.
An authentication failure may not be a vulnerability if user access is prevented due to a technical glitch e.g., Two-factor Authentication (2FA) is implemented and the One-time Password (OTP) fails to generate, which will prevent legitimate user access but not allow an unauthorised user to gain access. Such a glitch, however, may still create a vulnerability if the system uses a fallback factor that isn’t secure.
8. Software or Data Integrity Failures
A software or data integrity failure occurs when code or data is treated as trusted without verifying if it is trusted. Examples include a vulnerability in a legitimate plugin or compromised updates. Data can be manipulated to result in incorrect decisions or prevent detection of a cyberattack.
9. Security Logging & Alerting Failures
Logging of activity that could cause a security incident is essential for early detection of cyberattacks. The value in detecting an attack depends on how quickly and effectively the organisation responds to the attack, which can happen only if an alert is issued which depends on monitoring and analysis of logged activity. Any failure of logging (e.g., multiple failed login attempts, that may indicate a brute force attack, are not logged) and alerting (e.g., no alert on large data transfer which may indicate data exfiltration) will, therefore, significantly inhibit enterprise defences and increase the destructive impact of an attack. K7 InfiniShield mitigates log-related concerns by gathering logs from across the enterprise digital ecosystem, enriching the logs and storing them in the K7 InfiniShield cloud, and enabling analysis of archived and real-time logs in the K7 InfiniShield SIEM; alerts prioritised by criticality ensure quick response while avoiding alert fatigue; customisable playbooks enable response orchestration and cybersecurity process automation.
10. Mishandling of Exceptional Conditions
IT infrastructure should be able to handle unusual or edge-case scenarios that were not considered in design or development. Mishandling of outlier events may result in potentially malicious outcomes (vulnerabilities) or cause operational disruption (crashes). Mishandling of Exceptional Conditions is a new category that has been introduced in OWASP Top 10 2025. The unusual combination of events and circumstances required to trigger mishandling may result in these vulnerabilities existing for a long time without being addressed, providing a large window of opportunity to an attacker. The term ‘Mishandling’ in this context refers to anything that may lead to an attack including error messages that contain information which threat actors can use to compromise an organisation and disruption due to unanticipated volumes of data traffic.
Mitigation measures include comprehensive evaluation of the design before development commences, and periodic penetration testing after deployment to identify trigger events and the potential impact of mishandling.
VAPT Prioritisation
Even with this list, enterprises may still struggle to identify and close security gaps due to lack of qualified talent and investigative tools. Performing a Vulnerability Assessment and Penetration Testing exercise that prioritises the elements of the OWASP Top 10 will help businesses identify weaknesses in their cyber defences and secure their operations against the threats they are most likely to encounter, significantly reducing their risk profile.
K7’s Vulnerability Assessment and Penetration Testing (K7 VAPT) methodology is aligned with the OWASP Top 10 and backed by K7’s multi-decade expertise in cybersecurity, ensuring our customers are protected against the most critical threats. K7 is empanelled by CERT-In for providing Information Security Auditing Services. Contact Us to learn more about how K7 can help secure your enterprise against the destructive impact of both common and unusual cyberattacks.









