The Rise of QRishing: A Brief Overview
QR (Quick Response) code-based phishing was especially popular after the COVID-19 pandemic when people got accustomed to QR codes, a matrix for stowing primarily web address-related data, for making contactless payments. Despite its current surge, QR code phishing, also known as Quishing or QRishing, has long been a problem, starting not long after smartphones became prevalent in our daily lives. These vicious campaigns take advantage of the popularity and usability of QR codes, causing consumers to become confused and concerned.
Earlier threat actors triggered QR code-based phishing to reroute victims’ smartphone traffic to a rogue website, and they kept it limited to smartphone users only, except in one campaign where the phishing email behind the cloak of legitimate shipping companies such as DHL asked recipients to send money via scanning a rogue QR code embedded in the email. However, the campaign disappeared in early 2022. Recently, a phishing email disguised as a legitimate company containing a QR code has rippled in the industry, hinting at how this innocent-looking phishing technique can be triggered to execute a large-scale attack.
Why Threat Actors Employ QR Codes in Phishing
Threat actors are competent and always searching for methods to evade sophisticated detection methods. They are aware that sending fraudulent links through persuasive emails is less effective these days due to the advanced cybersecurity solutions available. But sending a picture instead of a link is a better technique for several reasons, including the present shield.
- The image file containing the malicious QR code is just an image; hence, no security product can flag it as unfavourable since the email doesn’t carry any malicious link. Decoding the QR image to find out where it is supposed to tunnel the traffic requires resource-heavy computer vision technologies to scan each image the client receives.
- But there is a catch. If someone has an advanced layer of security, such as K7 Mobile Security for Android and iOS, installed on their device. In that case, it can alert and block once the victim unknowingly scans a QR code and opens a malicious website.
- Scanning a QR code that someone received via email requires a smartphone for scanning, and after several cautions, users seldom install security solutions on smartphones.
The Spectrum of Possibilities in QR Code-Based Phishing Attacks
Buggy QR codes can piggyback multifarious scam campaigns ranging from stealing banking credentials, crypto wallet swiping, installing spyware or trojans, session or account hijacking, creating initial access or backdoors for large-scale enterprise attacks, and many more.
Delving into QRLJacking: A New QR Code-Based Attack
QRLJacking Attack, short for Quick Response Code Login Jacking, is a relatively new type of cybersecurity attack that targets the system of authenticating users through QR (Quick Response) codes.
Here’s how it works:
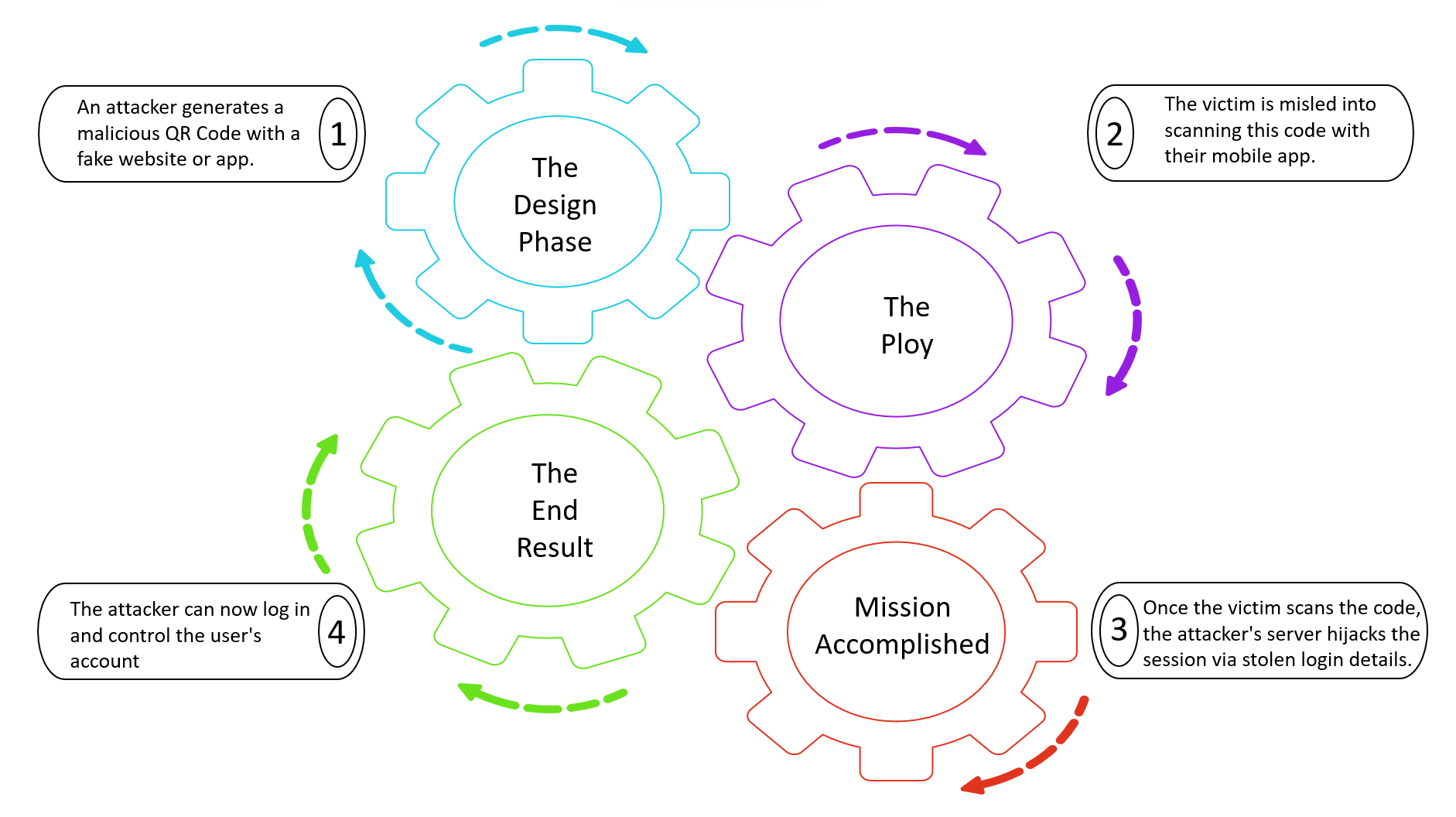
A successful QRLJacking attack can also snitch critical information about the device and the location, which the threat actors can later implicate.
Practical Steps to Counter QRishing and Quishing Threats
The rise of scams related to QR code phishing is alarming, with malicious players expected to devise more innovative ways to misuse QR codes. To counter these threats, high-end security tools like K7 Mobile Security can block most such attacks, but it also depends on avoiding simple mistakes. Hence, we recommend several steps to prevent these possible security threats.
- Confirm that the links provided by governments or other official entities are authentic before sharing personal information. Be sure to check URL spelling accuracy.
- Be cautious when scanning QR codes in emails, even if they appear from trusted organisations or individuals. Use multi-factor authentication for your bank, work, and other accounts to protect your login details.
- Be observant when using a merchant’s QR code; ensure that it’s not a fake one covering the original.
- Use QR codes for payments only with trustworthy merchants, service providers, or people you know.
- Be vigilant about app permissions; granting some of them can be risky.
- Install credible and advanced mobile security software like K7 Mobile Security, which can warn you about harmful sites.
- Establishing two-factor authentication adds a second layer to your account, minimising unauthorised access.
- Employers should conduct training programmes to educate them about new attacks, like QR code phishing, among other cyber threats.











