How attackers monetise cyberattacks and how they can be thwarted
Cyberthreats don’t just grow – they explode. AV-TEST registers over 350,000 new malware every day. A hacker attacks every 39 seconds.
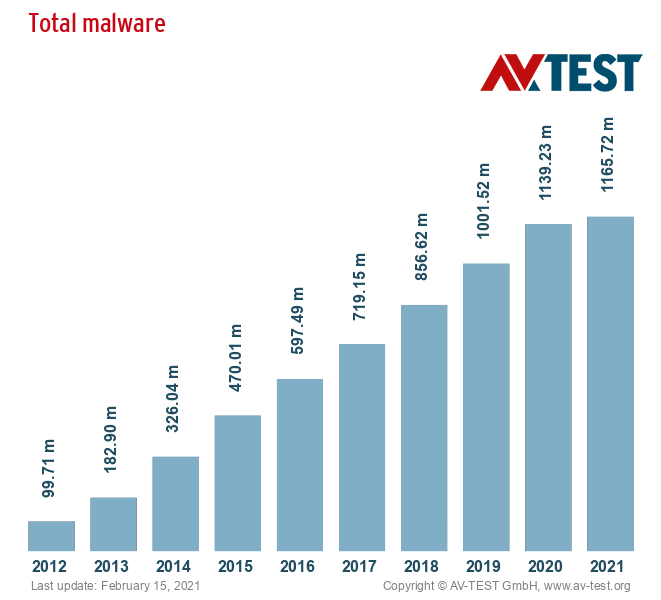
Source: AV-TEST
Such growth, and the increasing sophistication of cyberattacks, indicate powerful incentives are at play. The incentive is money – it’s a $1.5 trillion industry. But how is a cyberattack turned into money?
The Business of Cybercrime
Threat actors have a variety of ways to turn their cyberattack capability into a thriving business.
- Trading – Data gathered from a cyberattack can be sold on the dark web. Credit card data sells for up to $110, and full medical records sell for up to $1,000. Almost all data that is confidential or needs to be securely held can be sold
- Extortion – Even if the data does not have value to others, it will have value to the organisation that generates it, such as data that is required to conduct day-to-day operations. Ransomware attacks can encrypt this data and offer the decryption key on payment of ransom (usually in untraceable cryptocurrency). Nayana paid $1 million to unlock their computers. DDoS attacks can also be similarly monetised, demanding a ransom to call off the attack
- Employment – Threat actors offer their services to others for a fee, and can earn salaries as high as $1 million per year. They can be hired to engage in
- Sabotage
- IP Theft
- Industrial Espionage
- Cyberwarfare
- Services – Threat actors develop cyberthreats, such as ransomware or a botnet to launch DDoS attacks, then package them as services and advertise them on the dark web similar to legitimate Software as a Service (SaaS) offerings, which less proficient attackers can use
The amount of money involved and the relative ease with which an attack can be monetised make an attack on your organisation inevitable. There are several steps you can take to protect your business, which we will discuss here.
Thwarting a Cyberattack
- Create a Cybersecurity Policy – A cybersecurity policy lays down objectives, roles, responsibilities, and standards. It allows you to define what cybersafety looks like for your organisation, and then create the required hard and soft infrastructure to achieve that vision. It is important to ensure policy compliance across the entire organisation to avoid the policy merely existing on paper. This cybersecurity policy template can be used as a guide to framing a policy for your organisation
- Take Frequent Backups – Having a recent data backup avoids the need to pay a ransom in the event of a ransomware attack. Periodically check that backed up data can be restored quickly to ensure minimal disruption to your operations
- Invest in Training – Alert and informed users are the best defence against social engineering attacks like phishing which target users rather than devices or networks. Training on cyber hygiene and cybersecurity fundamentals acts as a preventive measure against many cyberthreats, stopping them before they can start
- Segment Networks – Divide your network into segments, and restrict access to each segment to those whose responsibilities require access to IT assets within that segment. This can contain an attack within the network segment and prevent it from spreading across the organisation
- Revoke Access on Exit – Employee exit management should include revocation of physical and digital access to the organisation’s IT assets. This blocks a disgruntled former employee from launching an attack and prevents external threat actors from exploiting unused employee accounts
- Conduct Security Audits/VAPT – Performing a security audit or Vulnerability Assessment and Penetration Testing (VAPT) will help identify malware entry points and other weaknesses in the organisation which should then be closed
- Deploy Endpoint Protection – Installing a capable cybersecurity solution, like K7 Endpoint Security, on endpoints will prevent threats from taking hold of devices and then spreading within the organisation. Enterprise endpoint security usually has centralised management which enables quick responses to security incidents
- Deploy Network Security – Utilising gateway security devices, like K7’s Unified Threat Management appliances, provides robust access control, user authentication, secure site-to-site communication, and network- and application-level protection
- Plan for a Cybersecure Future – Building cybersecurity into the fabric of your organisation will make it much more secure than adding it later as a layer. Adopt a ‘cybersecurity first’ posture when creating new processes, procuring new hardware and software, and setting up new facilities.
K7 Security’s Endpoint Security and Unified Threat Management enable SMEs and large organisations to secure their IT infrastructure without affecting device or network performance. Contact us to learn more about how we can help you thwart cyberattacks and protect your operations.











