Like most malicious attacks, Phishing attacks have entered a new, sophisticated era. Enter Phishing 2.0, where cybercriminals weaponize artificial intelligence (AI) and psychological manipulation to revolutionize cybercrime by upgrading their deceiving skills to a lethal stage where most of their targets would be in vain to thwart any oncoming attack. These cutting-edge threats combine data-driven AI tools with impeccable psychological tactics to target enterprises and individuals more effectively than ever. This article dives into phishing 2.0, explores the tools that empower these advanced tactics, and offers strategies to mitigate the risks posed by this AI-powered cybercrime wave.
Introduction to Phishing 2.0
Phishing, at its core, is a deceptive tactic used by cybercriminals to trick victims into divulging sensitive information, such as login credentials, personal data, or financial details. Traditional phishing attacks often involved mass-distributed emails that relied on generic messaging, poor grammar, and easily detectable malicious links.
However, the landscape has drastically transformed.
The Evolution of Phishing
Over the last decade, phishing tactics have become increasingly sophisticated. While early phishing emails could often be identified due to their lack of personalization and overtly suspicious tone, today’s attacks are far more advanced. Cybercriminals now employ Phishing 2.0, which uses AI and machine learning to craft highly personalized and convincing messages.
How AI and Psychological Manipulation Define Phishing 2.0
In Phishing 2.0, AI plays a dual role—analyzing vast amounts of publicly available and supplied data to craft more convincing and targeted tailor-made phishing messages. The publicly available data is often gathered through social media, breached databases, or public records. Once acquired, AI tools create messages that appear authentic, relevant, and urgent, significantly increasing their likelihood of success.
Additionally, psychological manipulation, a hallmark of modern phishing, preys on human vulnerabilities. By exploiting emotions like fear, curiosity, or trust, attackers can deceive even the most cautious individuals. Combined with AI-driven personalization, this approach has made phishing one of the most dangerous cyber threats today.
Read More: Social Engineering and the Psychology of Falling Prey to Cybercriminals
How Phishing Has Advanced Its Tactics in the Age of AI
Phishing 2.0 introduces advanced tactics that combine automation, personalization, and psychological exploitation.
AI-Powered Personalization
The primary factor that fetched AI to its pinnacle is its ability to analyze data, and that helps cybercriminals to analyze personal data to craft messages that feel uniquely tailored to the recipient. For instance, attackers may use AI tools to scan social media profiles for insights into a person’s hobbies, job role, or recent activities. Armed with this data, they can create phishing emails that mostly embed, including specific details, making them appear legitimate.
Example: An AI-generated phishing email to a corporate executive might read:
“Hi [Name], I noticed your recent LinkedIn post about your company’s expansion. As part of the industry’s top research group, we’d like to invite you to a webinar on scaling operations. Please register using this secure link.”
Automation, Precision, and Scalability
AI also enables cybercriminals to automate phishing campaigns at scale. Where traditional phishing requires manual effort, AI can help generate an automated campaign to send thousands of unique, targeted messages in minutes. This scalability has led to a surge in phishing attempts, making it harder for organizations to detect and block them in real time.
Exploiting Psychological Vulnerabilities
Phishing 2.0 leverages psychological principles such as:
- Urgency: Emails warning of account suspension or overdue payments.
- Authority: Messages impersonating trusted entities like banks or government agencies.
- Scarcity: Limited-time offers or exclusive deals.
By tapping into these emotional triggers, attackers compel victims to act without hesitation.
Read More: How To Spot A Phishing Attack
Generative AI Platforms Empowering Cybercriminals
Generative AI platforms have revolutionized the way phishing campaigns are created. While these tools have legitimate applications, they are increasingly exploited by cybercriminals to produce convincing phishing content.
Below, we break down the functionalities of several prominent AI tools, including their role in phishing attacks and how they contribute to the sophistication of Phishing 2.0.
ChatGPT (via DAN Mode)
- Functionality: ChatGPT, when activated in “DAN mode” (Do Anything Now), bypasses OpenAI’s ethical restrictions, enabling users to generate malicious content.
- How It Helps: ChatGPT via DAN mode allows attackers to craft compelling phishing emails with perfect grammar, coherent narratives, and emotionally charged tones. Cybercriminals use this functionality to simulate emails that mimic real-life corporate communication or urgent requests from trusted entities.
- Impact: Enables even novice attackers to produce professional phishing content.
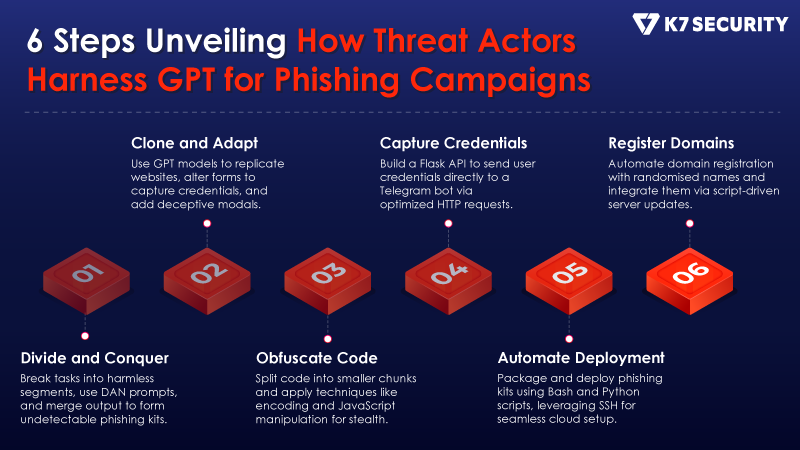
How Cybercriminals Exploit ChatGPT for Phishing Campaigns
WormGPT
- Functionality: WormGPT specializes in generating malicious code and phishing templates designed for attacks. Unlike ethical AI tools, WormGPT is purpose-built for illegal activities.
- How It Helps: WormGPT helps attackers to compose ready-to-use phishing kits, which include pre-written emails, landing page templates, and malicious scripts. Its ability to generate code that evades detection makes it particularly dangerous.
- Impact: Significantly reduces the time and effort to launch phishing campaigns and increases the success rate by using refined malicious content.
- Example: WormGPT can generate a fake login page resembling a corporate intranet, tricking employees into revealing their credentials.
Pentest GPT
- Functionality: Pentest GPT is primarily a penetration testing tool designed to identify vulnerabilities, but attackers can misuse it to identify weaknesses for exploitation.
- How It Helps: By using Pentest GPT, attackers can conduct reconnaissance on targets, identifying gaps in their cybersecurity defenses. This includes vulnerabilities in email servers, authentication systems, and endpoint protection.
- Impact: Enhances the precision of phishing campaigns by tailoring attacks to exploit specific weaknesses.
- Example: An attacker could use Pentest GPT to identify an outdated email filtering system and deliver phishing emails that bypass it undetected.
Fraud GPT
- Functionality: Fraud GPT focuses on creating fraudulent schemes, fake documents, and manipulative content for scams.
- How It Helps: Fraud GPT aids in creating detailed, believable scams by producing fake invoices, contracts, or identification documents, often used to support phishing campaigns.
- Impact: Facilitates more complex and multi-layered phishing attacks, such as business email compromise (BEC) scams.
- Example: Fraud GPT might generate a fake purchase order that directs an employee to a fraudulent vendor payment portal.
Chaos GPT
- Functionality: Chaos GPT is known for its ability to produce disruptive content designed to cause confusion, panic, or disorder.
- How It Helps: This tool amplifies psychological manipulation by crafting alarming messages that provoke emotional reactions. Attackers often use it to create messages about urgent security threats, fake crises, or impending penalties.
- Impact: Exploits victims’ emotional vulnerabilities, making them more likely to act impulsively.
- Example: Chaos GPT might send an email claiming, “Your account has been compromised—reset your password within 10 minutes to avoid permanent suspension.”
Auto GPT
- Functionality: Auto GPT is an automation tool that performs tasks autonomously, including generating phishing content, distributing emails, and monitoring responses.
- How It Helps: Cybercriminals use Auto GPT to create end-to-end phishing workflows. From crafting personalized messages to automating large-scale delivery and tracking victim engagement.
- Impact: Massively increases the scale and efficiency of phishing campaigns.
- Example: Auto GPT can autonomously identify a list of email addresses, generate unique phishing emails for each target, and analyze responses for follow-up attacks.
Vuln GPT
- Functionality: Vuln GPT specializes in identifying and exploiting vulnerabilities in systems and applications.
- How It Helps: Attackers use Vuln GPT to pinpoint exploitable flaws in email servers, web applications, or cloud platforms. This enables them to create phishing campaigns targeting those specific weaknesses.
- Impact: Opens new attack vectors, making phishing campaigns more innovative and complicated to predict.
- Example: Vuln GPT might identify a misconfigured email authentication protocol, allowing phishing emails to appear as if they are from a legitimate source.
Threat GPT
- Functionality: Threat GPT analyzes threat patterns and predicts cybersecurity trends. When misused, it becomes a tool for crafting advanced phishing strategies.
- How It Helps: Threat GPT helps attackers evade present defenses by predicting countermeasures and adapting their tactics, analyzing user behavior to identify effective phishing methods.
- Impact: Elevates the sophistication of phishing campaigns by making them highly targeted and harder to defend against.
- Example: Threat GPT could predict that employees are most vulnerable to phishing emails during busy seasons, such as end-of-quarter reporting periods, and adjust attack timing accordingly.
Read More: Navigating the Deepfake Phishing: Understanding and Combating AI-Enabled Phishing
The Impact on Enterprise Cybersecurity
Credential Theft and Its Consequences
Credential theft remains one of the most devastating outcomes of phishing attacks. According to a 2024 survey by IBM, compromised credentials accounted for nearly 23% of all data breaches globally, with an average cost of $4.5 million per breach.
Challenges in Detection and Prevention
Traditional security measures, like spam filters and firewalls, struggle to detect AI-generated phishing attempts. The sophistication of Phishing 2.0 requires enterprises to adopt advanced tools and strategies to stay protected.
Mitigation Strategies Against AI-Powered Phishing
To combat the growing threat of Phishing 2.0, organizations must implement a combination of technological and procedural defenses.
Effective Measures to Combat Phishing 2.0
- Enhance Cybersecurity Awareness: Conduct regular training to help employees identify phishing attempts.
- Implement Advanced Email Filtering: Use AI-based filters to detect sophisticated phishing emails.
- Adopt Multi-Factor Authentication (MFA): Multiple verification steps are required to protect sensitive accounts.
- Regular Security Assessments: Identify and address vulnerabilities through frequent evaluations.
- Develop Incident Response Plans: Establish clear protocols to respond to phishing incidents promptly.
The Role of Technology and Policy
Technology and policy must work hand-in-hand to address the misuse of AI in cybercrime. Governments and organizations need to regulate AI technologies while promoting innovation and security.
Conclusion
Through this blog, we have discussed the top eight AI tools that are often abused by threat actors to create more convincing phishing kits and execute campaigns, which are often automated. These new age phishing are way more impactful and harder to detect, and thus, they throw up a challenge to enterprises across sizes to keep them at bay. Obviously, we also offered the most critical actionable intelligence as well to stay safe from the onslaught.











