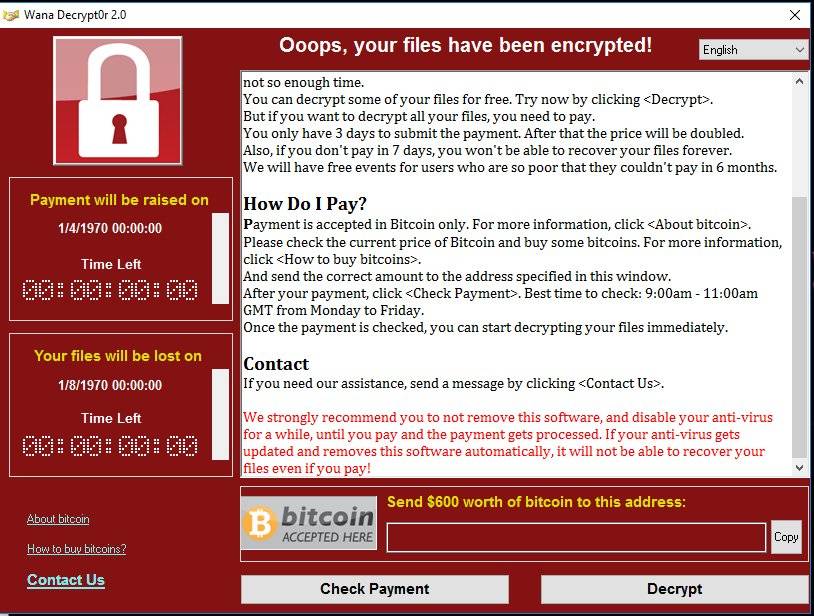
After the aftermath of WannaCry, the insecurity, and the panic seemingly calmed down, media has other hot news to talk about now. Companies like K7 Computing stepped up to the occasion and released a free scanner to check if your computer is infected.
WannaCry, must be credited as one of the most successful ransomware in history. The speed with which they have exploited the vulnerability and the effectiveness of the attack is praise-worthy, unfortunately, the criminal intent refrains us from praising them, but we have to thank them for another wake up call.
The media had a field day the past weekend, from describing Ransomware to getting opinions from experts and so called experts. This obviously has led to a lot of false information and a general panic. Keeping a few things in mind will keep you abreast of the situation and also set the record straight with minimum misconceptions.
Facts about WannaCry :
- Encrypts the data and offers the decrypt code for a price (a ransomware).
- WannaCry exploits an MS17-010 vulnerability to distribute itself. This is a critical SMB vulnerability with remote code execution options, and the exploit for it is also known as the ‘EternalBlue’ exploit. It is also possible that WannaCry can arrive via email, either as a malware attachment or as a malicious link.
- The international antivirus fraternity, including K7 Computing, is working towards creating a decrypt code to retrieve the data; which should be made available at the earliest. In the current scenario, the users will have to opt for a diagnostic solution and a preventive solution.
- This ransomware can spread to all Windows OS prior to Windows 10 particularly the outdated/ not-supported OS. Also vulnerable are those newer OS’s that have not been updated with the latest patch/update. If allowed to launch, e.g. from a malicious email attachment, WannaCry would still successfully encrypt files even on a fully-patched Windows OS, whether Windows 10 or earlier.
- So-called password that was mentioned by so-called-experts does not work. It is recommended not to try them as they technically initiate a process that aids in the spreading of the virus.
- Although from an external source, this attack is still considered to be an insider/internal attack based on its behavioral pattern.
- Effect on ATMs: Most ATMs usually use old OS versions which are not updated/patched regularly, and if they are connected to the internet, they are at high risk of exploitation.
Recommended diagnostic action: Scan the machine with the free K7 WannaCry scanner (available at www.k7computing.com). It is important to know if your system is infected. This scanner basically scans your system identifying any WannaCry files and removes them from the machine. The K7 Computing WannaCry scanner also identifies and removes other dangerous ransomware and bots. No need to alter or disable your existing security product. This scanner works without interfering with your current settings.
Recommended preventive action:
- Clean your system with the K7 WannaCry Scanner to remove infected files, thus preventing further infection, spread and damage.
- Update/install all OS updates/patches. Microsoft has released patches even for the no-longer-supported Windows XP considering the magnitude of this attack. (Links to Windows patches). It is recommended to activate automatic updates.
- Avoid pirated Operating Systems.
- Take a regular backup, preferably on an external device/ cloud.
- Do not run any file from an unknown source.
- Use a good up-to-date security software (generally not free)
- Keep yourself updated on the latest security issues and solutions.
About the free scanner: The free scanner will work with any other antivirus product, it does not require installation and can run even from a USB pen drive. The scanner can be used by enterprises to scan all incoming emails and files being copied onto their systems.
Free Public support: K7 Computing has also initiated a dedicated help desk offering free support and help to users of other security products (1800 4190077)