Compromising passwords is not a new thing for hackers. With every passing week, we hear some news or the other of such a breach. But are the hackers only at fault? Though we read numerous instructional articles on the importance of choosing passwords with great combinations, we are either too lazy to modify the existing ones or act too naïve. As a result, the hack happens that compromises all your data, including essential files.
And the headache is that much more for large groups with legions of users across the globe. The victim’s of numerous cyber breaches often not bother to modify their passwords even after the breach.
- The best way to keep yourself secure online is to hash your passwords. The process encrypts your password in such a manner that can’t be predicted without its hash. The only way to find out the password is to use the rainbow table—a pre-computed table for reversing cryptographic hash functions.
- Another secure method is Salting, which involves adding a random character after the password and then hash it.
- The idea is to either hash or salting your passwords to keep them safe in a password manager, and there are several free tools online to execute the two strategies.
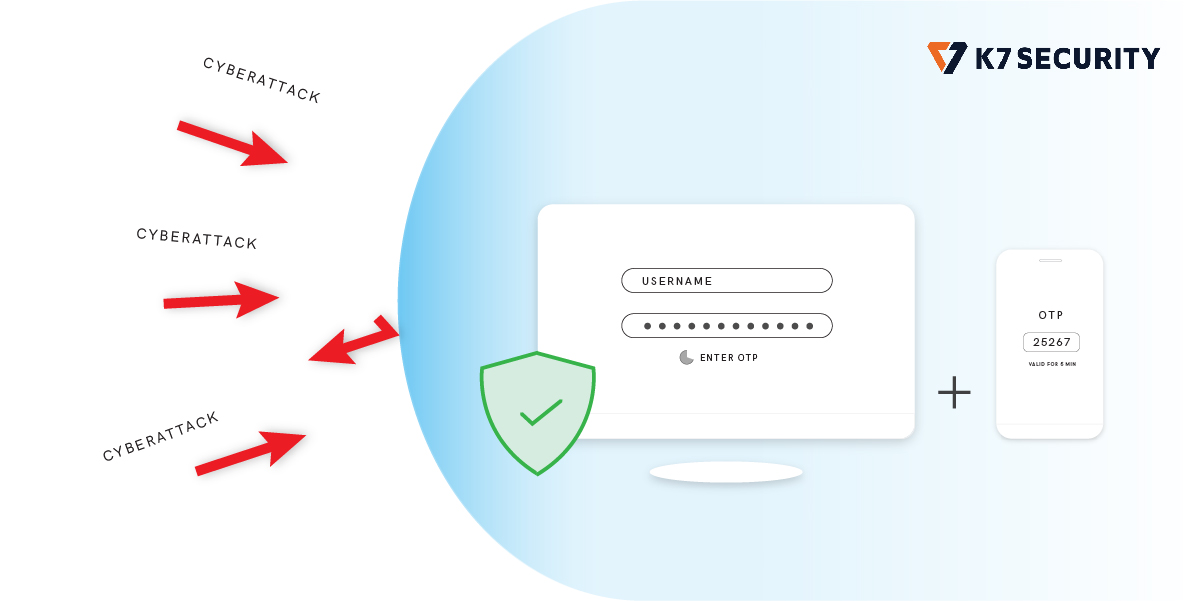
- If you feel the process is too complicated, then try an app like Google authenticator for all your non-Google accounts. The app creates a 2-step verification code to protect your account from hijacking by adding another layer of security. With 2-step verification, signing in will require a code generated by the Google Authenticator app in addition to your account password.
- If you find Google Authenticator is too complex to use, then we recommend you to use an app called Authy. The app is designed with an everyday consumer in mind—you’re still protected if you lose your phone, change numbers, or add new devices. Authy securely backs up your account data in the cloud instead of handing you a block of backup verification codes.
- You can also choose a complex password using password generator tools and save them in any password manager. There are several password managers available for every platform, and many of them are cross-platforms too. Some such examples are LastPass, Keypass and 1Password.