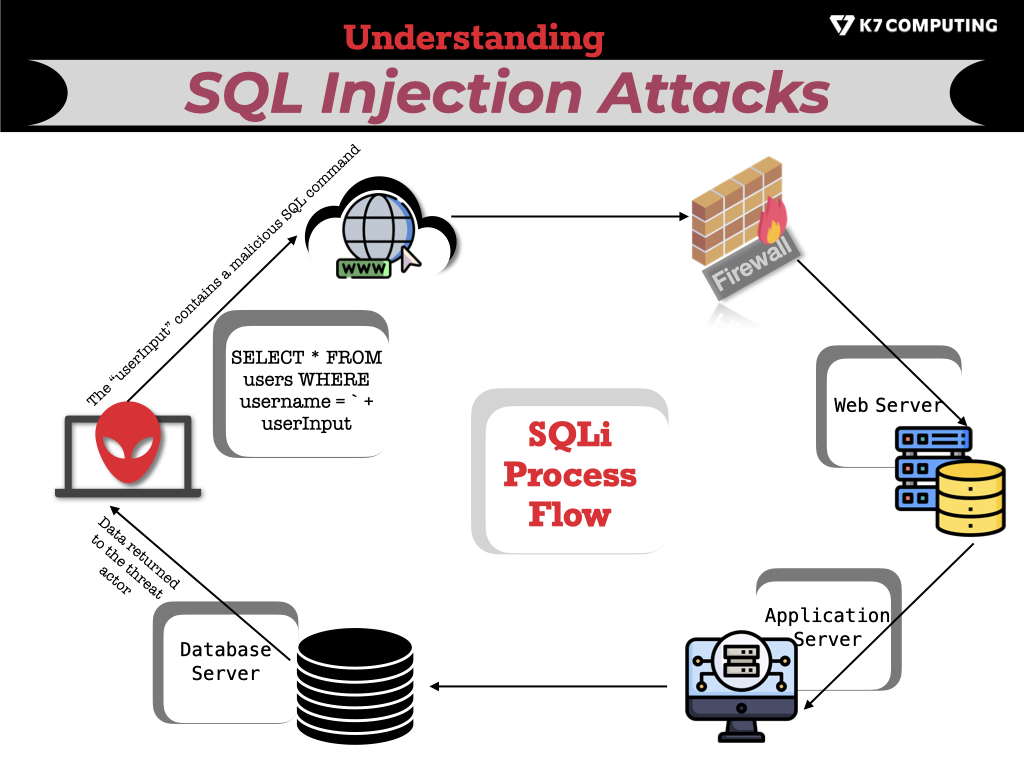
What exactly is SQLi?
SQL Injection alias, SQLi (Structured Query Language Injection), leverages malicious coding techniques to inject SQL commands into a vulnerable website or application’s database, allowing them to retrieve data from the database or modify its contents. This technique enables threat actors to steal account credentials, alter account information, and perform other malicious actions.
SQLi can also help an attacker execute commands on the operating system to help them escalate to more severe attacks within a network protected by a firewall.
Why is SQLi so popular among cybercriminals?
Attackers use SQL Injection due to its ease of execution and ability to grant unauthorized access to sensitive data contained in a database. SQL injection attacks involve injecting malicious SQL queries into an application’s input fields, causing the database to execute unintended commands.
SQL injection attacks can steal or change data, circumvent login credentials, and execute commands with elevated access. In addition, SQL Injection may be performed using readily accessible and automated technologies, making it a popular choice among even rookie attackers.
Standard methods used by attackers to exploit SQLi vulnerabilities.
The three major SQL Injection categories are In-band SQLi, Inferential SQLi, and Out-of-band SQLi.
In-band SQLi
Among all forms of SQLi attacks, In-band attacks are the most prevalent method where an attacker utilizes one channel to execute the attack and accumulate the output data.
In-band SQLi attacks can be grouped into two types of in-band SQL Injection: Error-based SQLi and Union-based SQLi.
Union-based SQL Injection: In this method, the attacker uses the ‘UNION’ operator in the SQL query to inject their malicious code to retrieve information from the database.
Error-based SQL Injection: The attacker tries injecting the code into the query, which returns errors that could provide valuable information about the database schema or the table values.
Inferential SQLi
Even though exploiting Inferential SQLi can be time-consuming, it is still highly prevalent. In these SQLi attacks, the malicious actor can recreate the database structure by sending payloads, analyzing the web application’s response, and determining the database server’s behavior. Boolean-based Blind SQLi and Time-based Blind SQLi are inferential SQL injection types.
Boolean-based SQL Injection: In this method, the attacker uses boolean conditions to exploit vulnerabilities. The attacker will try to guess the right conditions using true/false statements.
Time-based SQL Injection: In this method, the attacker abuses the response time in the SQL query when the database processes the request. By injecting time delays, the attacker can infer results and learn more about the database and server.
Out-of-band SQLi
The Out-of-band SQL Injection method is not very popular, and its success rate depends on the number of available features turned on in the web application’s database server. However, out-of-band methods provide an alternative to inferential time-based approaches for an attacker, which is especially useful in situations where the server answers are unpredictable.
Blind SQL Injection or BSQLi
BSQLi stands for Blind SQL Injection attacks which send true or false questions to the target victim’s database and determine the response based on the application’s response. This method is commonly employed when a web application is configured to display generic error messages but has not mitigated SQL injection-vulnerable code.
BSQLi is a severe security threat as it can allow an attacker to retrieve sensitive data, modify or delete data in the database, or even gain control over the entire application. We will come up with a detailed blog on this topic.
The consequences of successful SQL Injection attacks.
SQL Injection attacks occur when malicious actors inject malicious SQL code into vulnerable websites, web applications, or databases, allowing them to access or manipulate sensitive data, steal confidential information, or even take control of the affected systems.
The consequences of successful SQL Injection attacks can be severe and devastating, including:
- Data Theft: Attackers can gain access to and steal sensitive data, including personal, financial, and medical information of individuals, as well as confidential business data, such as intellectual property, trade secrets, and financial records.
- System Disruption or Downtime: SQL Injection attacks can also cause system disruptions or unavailability, resulting in a loss of productivity or inability to access critical services.
- System Hijacking: Malicious actors can gain unauthorized access to critical systems or networks, resulting in system hijacking or takeover.
- Account Takeover: Threat actors often prefer SQLi attacks for account takeover because they bypass standard authentication methods and gain unauthorized access to sensitive information.
- Reputational Damage: Successful SQL Injection attacks can tarnish an organization’s reputation and erode customer trust, leading to loss of business opportunities and customer churn.
- Legal and Regulatory Consequences: Companies that fail to protect their systems from SQL Injection attacks could face significant legal and regulatory consequences, including fines, penalties, and sanctions.
The role of education and awareness in preventing SQL Injection attacks.
Education and awareness are essential in preventing SQL Injection attacks. Software developers, system administrators, and end-users must be aware of the potential risks and vulnerabilities that SQL Injection attacks pose to their systems and applications.
One of the primary ways to prevent SQL Injection attacks is by educating developers and administrators about best practices in coding and SQL injection prevention. These practices may include using prepared statements, input validation, parameterized queries, and other techniques to protect against SQL Injection attacks.
End-users also have a vital role to play in preventing SQL Injection attacks. First, they need to be aware of the potential for malicious actors to exploit vulnerabilities in poorly protected systems and applications. By being cautious about clicking on suspicious links or downloading files from unknown sources, users can help to prevent various attacks to a great extent.
How to Prevent SQL Injection Attacks?
The following are some recommendations to prevent SQL Injection Attacks:
- Parameterized Queries:
Developers can use parameterized queries to prevent SQL injection attacks. In parameterized queries, they would write SQL codes with variables representing the data that the user enters on the website or application. These variables would be validated first and then verified against the database, which rules out the possibility of malicious code being injected through texts.
- Input validation:
Developers should incorporate input validation to ensure that the data entered by the user fits a particular format or category. Enterprises must implement this input validation both on the client and server sides. For example, one way to prevent SQL injection is to avoid accepting any input that is not a number or an alphabetic character.
- Stored Procedure:
Stored Procedures have different syntax and are not vulnerable to SQL injection attacks; hence, they can be used as an alternative to embedding SQL directly inside a code.
- Restricting Database Permissions:
Database user role management policies can grant different permissions to different database users based on their roles. Therefore, it is advisable to assign different permissions, which restrict or limit the use of SQL commands and procedures, preventing SQL injection from arbitrary database manipulation or exploitation.
- Security patches, Updates, and backups:
SQL injection prevention includes continuously monitoring and updating server-side code, platform, applications, and plugins. Corrective action should be promptly applied to any known vulnerabilities. A backup strategy must also be in place to recover from any compromise.
- Data Wrangling:
Even though data wrangling may not necessarily be the most effective method for mitigating SQL injection (SQLi) attacks, it can certainly maintain the quality and accuracy of data and prevent data breaches.
Final Words
In conclusion, preventing SQL injection attacks requires a holistic approach involving development, database administration, user education, and the purchase of the right tools.
Education and awareness are essential in preventing SQL Injection attacks. Educating developers, administrators, and end-users about potential attack vectors, best practices in coding and SQL injection prevention, and being cautious on the internet can immensely reduce the risk and impact of SQL Injection attacks.
The cybersecurity educational and awareness initiative of K7 Computing, called K7 Academy, conducts frequent seminars to improve the cybersecurity hygiene of organizations and SMBs. Also, you can contact us to do campaigns for your employees to increase cybersecurity awareness and stop attacks.











