This blog is a comprehensive guide to brute forcing attacks and how to protect your data from threat actors.
Before we delve into the what and how of it, let us get into a few basics.
What is a brute force attack?
Password hacking is a means by which threat actors attempt to crack login credentials and encryption keys. Brute force is one type of password hacking. It uses a trial and error method to bypass login credentials. It is a straightforward and predictable technique which breaches organizations and individuals data, thereby causing reputational and financial loss and disquietude to them.
Why do threat actors still prefer this?
This is a preferred method, as passwords will be found eventually given enough time. However, this attack is extremely slow to hack complex passwords. This is usually successful as users don’t follow proper cyber hygiene and choose easily guessable passwords or default passwords. Most of the security breaches happen due to this.
Types of brute force attacks
- Simple brute forcing
This is a manual process where in threat actors hack easily guessable and default logins. This is simple and hackers rely on users’ poor password hygiene such as using weak passwords like “login123” or using the same passwords for multiple accounts. This is a slow process.
- Dictionary attack
This method tries to guess login credentials by trying every possible word in the dictionary, knowing the individuals’ account details like name. Though relatively faster than simple brute forcing, it is restricted by the fact that a threat actor will be able to find the password only if it is from the dictionary. Though quicker, there may not be a 100% success rate.
- Hybrid brute forcing
This begins with threat actors’ knowing the individuals’ account details like name and using a combination of dictionary and simple brute forcing to guess the login credentials.
- Reverse brute forcing
In this case, the threat actor gets hold of the password through a network breach and then tries all combinations of user name’s to gain access to the login credentials.
- Credential Stuffing
In this attack, threat actors use the stolen credentials to pursue user’s following poor password hygiene practices to see if the same credentials are being used for their additional accounts too or if they are reusing the same passwords for various accounts.
Brute force attack tools
Penetration testing is for testing and strengthening the network security of an organization and various commercial/open source tools have been developed for the same. Brute force attack tools were developed for automating the credential guessing, as it is a time intensive process. However, such tools are now being used for nefarious purposes. Popular ones are listed below.
- Aircrack-ng
A suite of tools that assesses and hacks Wi-Fi networks by monitoring packet capture and exporting data to attack an organization through fake access points and packet injection.
- John the Ripper
An open-source password hacking tool for many operating systems like macOS, Unix, and Windows. It primarily uses three modes to crack passwords viz. Single crack mode, Wordlist mode and Incremental mode. More on the cracking modes.
- Hydra
This tool is used to crack the passwords of various network protocols and web applications using dictionary attack. Popular protocols include telnet, FTP, HTTP, HTTPS, SMB, databases, and several other services.
Significant brute force breaches
Listing below are a few of the significant breaches due to poor password hygiene
- Canadian Revenue Agency Attack due to credential stuffing, a subset of brute force attack, compromising accounts of Canadian Revenue Agency and federal departments.
- SolarWinds Attack due to default and easily guessable passwords, a supply chain attack wherein the update server for SolarWinds’ Orion product was compromised to infiltrate into tens of thousands of organizations and steal data.
- Mallox Ransomware Attack compromised networks of the Federation of Indian Chambers of Commerce & Industry (FICCI) on February 23, 2023 causing huge data breach due to default and easily guessable passwords.
Vulnerable Entry Points
- RDP brute forcing
This protocol is exploited when an insecure network is used to access the RDP server, thereby allowing threat actors to infiltrate the session and gain access to the server itself.
Threat actors, for instance, can use ransomware after RDP brute forcing to spread laterally.
- DNS brute forcing
Threat actors try to discover all of the resources under a domain name. By knowing which resources are being used, threat actors try to find a vulnerable system in the network which can be exploited to gain unauthorized access. Using brute force, attackers perform DNS lookup requests for a large number of commonly used subdomains in order to discover services associated with the domain name. This type of attack usually sends out too many requests to invalid DNS record resources.
- SSH brute forcing
This is achieved by using a trial and error method on many servers until a match is found.
- SMB/CIFS brute forcing
File sharing protocols are prone to brute forcing. By finding weak login credentials threat actors can access files, move laterally, do privilege escalation among others.
- Telnet brute forcing
This is a relatively weak service that can be easily exploited. Threat actors usually exploit this using DDOS and other botnet related attacks
- FTP brute forcing
FTP is also easily susceptible to brute forcing as threat actors look out for default and commonly used login credentials. Threat actors also can guess the next open port and check whether any valid service is listening on that port and gain access by exploiting any vulnerabilities found in the service.
- Applications hosted on server
The Internet is scanned for vulnerable servers and applications. Threat actors usually look for services that are exposed to the public. Once the service is decided, they try to brute force themselves till they succeed. Once the service is breached, threat actors try to propagate laterally through the network.
Identifying a brute force attack
If anyone in your known circle has become a victim of this attack, request them to change their password immediately. Also, they should change the password of sensitive accounts such as financial accounts on a regular basis.
Let us now see how to spot a brute force attack.
- Multiple login attempt failure
- Multiple login attempts for the same username
- Login attempts with multiple username from same IP addresses
- Login attempts for a single account from different IP addresses
- Huge bandwidth consumption for a single session
- Failed login attempts from a specific pattern of username and password. For instance, following an alphabetic sequence
- Failed login attempts of commonly used passwords. For instance, qwerty, password123
Mallox Ransomware
Let us now see the proportion of K7 customers, grouped by vertical, who were affected by brute force attacks wherein the payload dropped was Mallox ransomware.
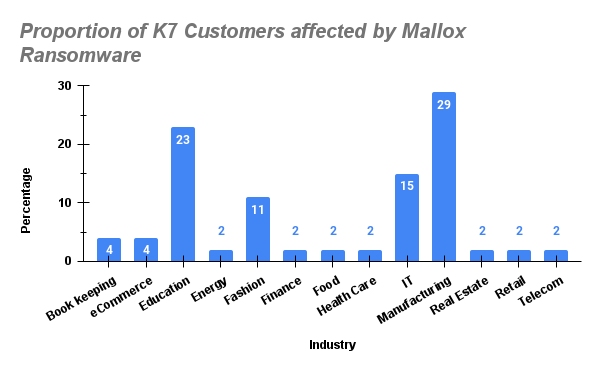
SMEs and MSMEs were the most affected by Mallox. Most impacted verticals were Manufacturing and Education, followed by the IT and Fashion industry. Let us now see why these sectors were affected in spite of warnings given.
- Manufacturing
These companies are a high-paying and a get-at-able target for threat actors mainly due to their low tolerance for an outage and not practicing good cyber hygiene practices.
Cyber attacks can be disastrous for their data and any compromise can ruin the organizations’ reputation and disrupt production which can cost the organization a lot.
- Education
This sector has been one of the most affected after the pandemic. WIth education going online, so are online payment methods and with scant regard for cyber security, any compromise not only causes a reputational loss for the educational institution; student’s privacy is also compromised.
- Industries having Personal Identifiable Information (PII) data
When threat actors target industries such as healthcare, finance, education, eCommerce and IT, apart from disrupting the organizations’ workflow, their primary intention is to steal and leak their PII data causing reputational and monetary losses to them.
- Fashion
Usually in this industry, threat actors use stolen credentials; things are bought and victims’ pay for it. Usually nothing is looted, making such crimes harder to uncover
Requesting all users to adhere to the early warnings and mitigation strategies from your security vendor, apply patches and keep your security software up to date to stay protected from the latest threats. Kindly do not ignore any early signs of breaches.
Proactive Protection @K7Labs
We provide proactive protection to all our customers based on the data gleaned from our K7 Ecosystem Threat Intelligence (K7ETI) infrastructure. We do this primarily to ensure that our customers do not miss out on any significant alerts that need to be actioned upon or where customers are not aware or are finding it difficult to mitigate.
Also, we not only provide general guidelines but also actionable items customized for every alert that needs to be mitigated.
Apart from this, we also share “Security best practices” with our customers on a regular basis.
Building a stout defense
Detecting a brute force attack may be easy due to the multiple failed login attempts. However, preventing the attack might not be as straightforward as blocking IP addresses from where the request is coming. This is because threat actors could use tools to make their multiple attempts appear to come from unique IP addresses.
That said, we are giving you certain useful tips to protect against brute forcing
- Enforcing a strong password policy
By using
-
- Longer passwords
- Using a combination of uppercase, lowercase, numerals and special characters to set your password
- Never reusing the same password again
- Setting a password expiry date
- Enabling Multi-factor Authentication (MFA)
In case of a 2FA, additional security can be provided by using a verification link or code, say one-time password (OTP) through SMS or email and allowing the user to login only after entering the same.
- Asking security questions
This can be used as an authentication mechanism after a fixed number of failed login attempts, as these make it difficult for threat actors to bypass these questions.
- Employing CAPTCHA usage
This prevents automated search submissions.
- Checking event logs for suspicious activity
Periodically checking for unusual login attempts may help system administrators to protect their organization network from a security breach.
- Account locking after a few failed attempts
Considering users’ safety, system administrators could restrict failed login attempts to say 5 attempts after which their account is locked. To unlock the same, they could employ any authentication method such as OTP and only if successful should they be allowed access.
- Locking out the IP address after a fixed number of failed attempts
System administrators could lock the IP addresses from where multiple failed login attempts happen. However, this approach might not be adequate if threat actors are using a botnet with many IP addresses for its bots.
- Delaying the response time between password attempts
If the response time between password attempts is delayed, so is the brute force attack giving system administrators time to take action.
- Using external services to check for a data breach
For instance, HaveIbeenPwned is a service that can be used to check multiple data breach repositories to see if your credentials have been compromised.
- Invest in good cybersecurity processes
Implementing best cyber security practices within your organization will go a long way in safeguarding your organization from threat actors waiting to launch attacks.
- Installing a reputable security product like one from the K7 Product series and keeping it updated to stay protected from the latest threats
- Patching your operating system and other devices against the latest vulnerabilities
Cyber security implementation is an ongoing process. Organizations need to upgrade their cybersecurity measures along with constant evolution in the cyber threat industry. The bottom line is that there is no single defensive strategy that one can adopt to prevent a brute force attack from taking place, as this attack varies on a case-by-case basis. However, one can adopt good cyber hygiene practices to avoid becoming a victim of such attacks.
Requesting you to share this blog among your friends and colleagues to understand and protect oneself from such attacks.
Read more on
SQL Server Brute Force Attacks Prevention, a detailed guide written by one of our industry colleagues.











