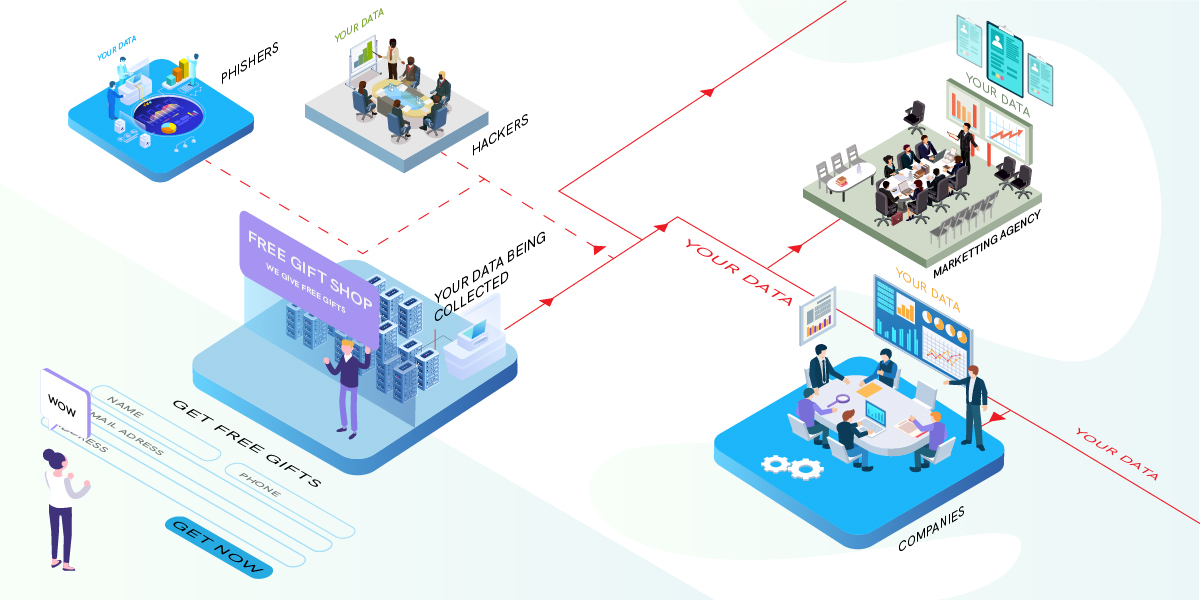
Volunteer Data, Breach of Trust
Recently, we were looking for an Android app in the Google Play Store to stream Jio TV content straight to a smart TV. Unfortunately, we couldn’t find any. We decided to continue looking for a suitable substitute and found a fitting one. We plan to use this example as a case study to explain how users are giving away their data by their own volition.
The blog sets out to describe how your personal information extracted from you, and later, could be used against you. Alongside, we will mention the safest means to safeguard yourself.
Let’s start rolling with some basic fundamental knowledge of a Data Breach.
What is a Data Breach?
Currently, ‘Data Breach” is the new buzzword in the Cybersecurity universe. In brief, Data-Breach details snitching sensitive and unauthorized information from enterprises and individuals by convincingly deceiving them.
Interestingly, many users seldom deliberate about the adverse outcomes the sharing of their personal information with unknown person/group and end up a victim.
Conventional methods of extracting Personal Identifiable Information (PII)?
The most common methods used in collecting Personal Identifiable Information (PII) is by diverting one’s attention onto something ostentatious:
Supermarket Offers
One of the most common ways for accumulating unwanted data is when people fall for the trick of exciting discount offers at the supermarket billing counter. The victim shares information and in return is bombarded by frequent text messages and emails from them, aimed at tempting the user to splurge on unnecessary items. Have you asked yourself what you get in return for sharing your information? If Credit Points is the answer which comes into your mind, you are living in a fool’s paradise. The credit points offer nothing beneficial except compelling you to spend more.
Online Shopping
In everyday life, most among us come across a myriad of online offers in exchange for our data like email, phone number, full name, and a lot more. We often give in those details without thinking twice about how the data will get used in the future.
But the question that arises here is why anyone would offer such crazy options? Well, let’s first understand, there is no free lunch in the world of internet. Even if you get something in exchange, they must be extracting something beneficial for them. Have you ever asked yourself about the reliability of the person at the other end? Ironically, we seldom investigate such offers and blindly trust alluring online entities often without cross-checking their authenticity.
Flashy Advertisement Campaign
Stop getting bedazzled at the random marketing campaigns at shopping malls. The jaw-dropping deals come your way is usually triggered to snatch your personal and sensitive data. In exchange for some merchandise or small token gifts, marketers accumulate your details like email ID and own phone numbers. In reality, these data are as valuable as your credit card PINs so always think twice before sharing with people you hardly know.
Let’s understand how we give away our data and device protection in exchange for some petty things.
Unlike these conventional offline methods for extracting PII information, the following observation details how the threat actors are accumulating your Personal Identified Information through a rogue app.
Our Observations
Once we found there is no app for streaming Jio TV content to Smart TV in Google Play Store, we headed to a third-party app store called APKMirror.
Luckily we found an app, mentioned to fulfil our requirements.
On downloading, we realized that the app comes with a default username and password. So the users’ would have to wipe it and write their own Jio credentials every time for opening the application.
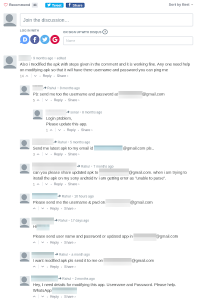
As expected, a large pool of users asked the author to edit the application. And in exchange, they shared their email ID and phone number. Moreover, they didn’t hesitate to share these credentials via WhatsApp either.
It brings up yet another critical question, what if a rogue mind injects some malicious code in this app and later impersonate them or do something more malicious? We are confident that people might install those infected APKs on their smartphones without hesitation.
How to circumvent such situations?
- Never share your personally identifiable information to any unacquainted person
- Try to avoid sharing your personal information, even if it looks mandatory. Find out some alternative method to ignore such a request
- Never download an app from third-party app markets
- Avoid posting personal information on public forums
- Never share any Government approved identity cards like Aadhar card, Pan Card, and Passport in exchange for any lucrative offer