A ransomware attack is a cyberattack where threat actors encrypt files on the victim organisation’s computers, rendering them unusable, and demand a ransom (usually in cryptocurrency) for the decryption key. The attackers may also exfiltrate data, which could include confidential information and Personally Identifiable Information (PII) of stakeholders, and threaten to release the data if the ransom is not paid.
Ransomware has become the preferred choice of cyberattackers as such attacks may have a very public, debilitating impact on business operations with widespread economic consequences, and have a monetisation model supported by nearly-anonymous cryptocurrency. K7’s whitepaper Unmasking Ransomware provides an in-depth examination of such malicious encryption.
Remote Ransomware
Conventional endpoint security solutions identify ransomware by analysing files and processes on the device in which the solution’s client is installed. Threat actors are aware of this approach and have created remote ransomware to defeat conventional cybersecurity solutions.
In a remote ransomware attack, threat actors discover an unprotected endpoint in an enterprise network and deploy ransomware in that endpoint. The remote ransomware process runs on the unprotected endpoint and attempts to encrypt files in shared folders (which can be accessed by the unprotected endpoint) on protected endpoints. The endpoint security solution in the protected endpoint is unable to identify and block the ransomware attack as it can only analyse processes that run on the same machine where the solution is deployed, but the remote ransomware process runs on another, unprotected, machine. This technique has emerged as an effective way for cyberattackers to defeat conventional cybersecurity solutions, with 60% of human-operated ransomware attacks using remote encryption.
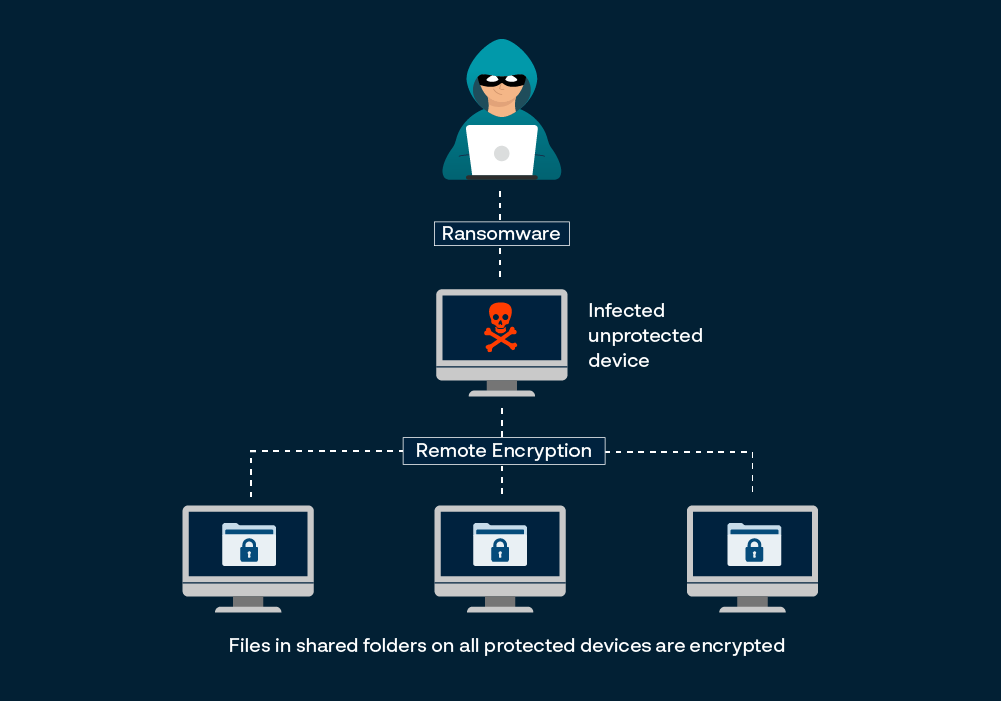
It should be noted that remote ransomware is not ransomware that is deployed through remote access tools such as Remote Desktop Protocol. While securing/disabling remote access will help prevent some ransomware attacks, it may not stop remote ransomware.
K7’s Ransomware Protection
K7 is an anti-ransomware pioneer, and was one of the first cybersecurity companies in the world to develop ransomware defences. K7 stops ransomware by combining signature-based detection, where signatures of known ransomware are determined, and behaviour-based detection which stops unknown/zero-day ransomware by monitoring potentially-suspicious processes and blocking them if they exhibit malicious behaviour.
K7’s ransomware protection achieved a perfect score in a test conducted by a security analyst where all protective layers other than behaviour-based protection were turned off, effectively turning all the ransomware samples used into unknown/zero-day ransomware, proving the effectiveness of K7’s ransomware protection.
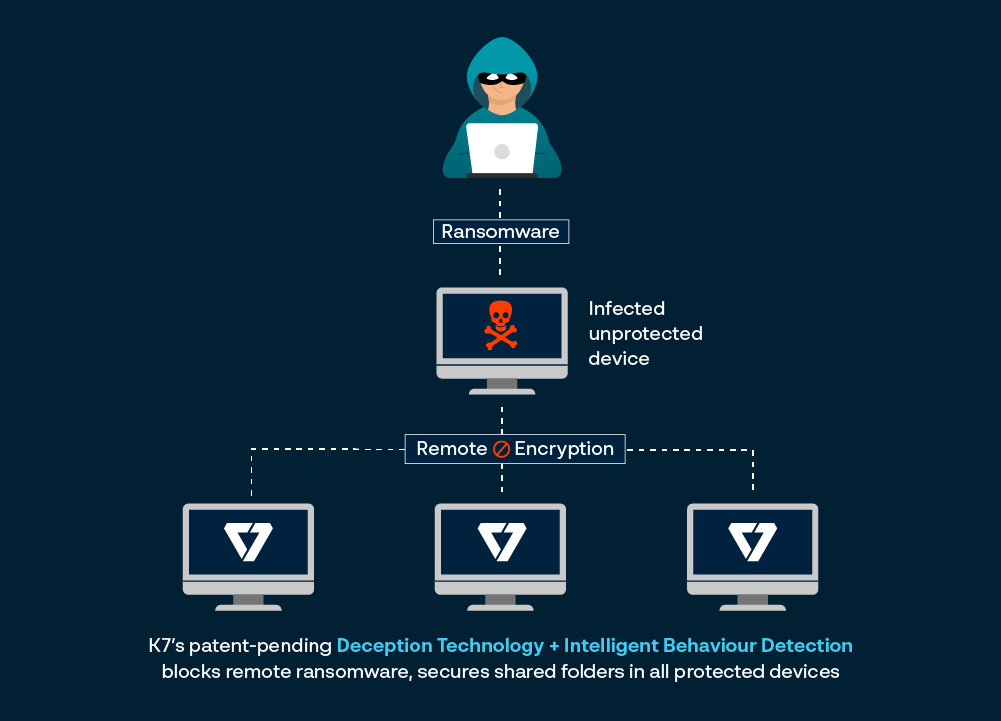
K7’s Deception Technology Stops Remote Ransomware
K7 has developed patent-pending Deception Technology which is combined with K7’s Intelligent Behaviour Detection to prevent remote ransomware attacks on devices protected by K7. Remote ransomware is identified and blocked and the organisation is protected through a multi-faceted approach that includes:
- Use of Decoy Files – Specially designed hidden files are deployed strategically in the protected device, including in shared folders, to serve as a decoy target for remote ransomware
- Automatic Blocking of Remote Device – The remote device that is launching the ransomware attack is automatically blocked from accessing the shared folder on the device protected by K7 to insulate the protected device from the ransomware
- Attack Alerts – Admins are immediately alerted that a remote ransomware attack has been attempted, with details of the attacking device, enabling them to immediately isolate the attacking device and prevent the attack from spreading to other unprotected devices in the business network
- Reports – Summary and Detailed reports for remote attacks can be generated, allowing admins to analyse such attacks and identify which aspects of the IT infrastructure require their attention to prevent recurrence of such attacks
Admins can configure these settings and automatically unblock the remote device after a set period of time has elapsed, or manually unblock the remote device once it has been disinfected.
K7 also offers many other advanced anti-ransomware features, including
- Enhanced Malware Startup Entry Cleanup – Ransomware is prevented from initialising through Startup Entries, Scheduled Tasks, and Windows Management Infrastructure (WMI) Event Subscription
- Enhanced Heuristics – Endpoints are monitored through enhanced heuristics to accurately identify ransomware and avoid false positives
- Anti-ransomware Policy Configuration – Admins can control these options, which include
- Forcing K7 user-mode services to start very early in the order of services ensuring that K7’s protection can initialise ahead of other services to protect them. Startup resources can be dynamically conceded to the operating system
- Safe Mode protection that ensures ransomware cannot attack a device even when it is started in Safe Mode. This protection is available in Network Only, Minimal Only, and Network and Minimal Only types of Safe Mode
K7 Endpoint Security incorporates K7’s state-of-the-art technology to protect enterprises against all forms of ransomware and many other cyberattacks. Contact Us to learn more about how we can help you secure your operations against highly destructive cyberthreats.











