Multi-Factor Authentication (MFA) is frequently presented as the ultimate solution to credential theft. We often see reports of cyberattacks that are blamed on a lack of MFA:
- A cyberattack on a petroleum products pipeline in the USA, which caused a 5,500-mile natural gas pipeline to be shut down for five days and more than 10,000 gas stations to be out of fuel, was caused by an unused VPN account that lacked MFA
- A ransomware attack on a healthcare revenue management system, which resulted in the leak of personal data of 100 million Americans, was caused by the compromise of a server that lacked MFA
- A 160-yearl-old logistics provider closed their doors due to a ransomware attack that was caused by a user whose account was not secured by MFA
However, believing MFA = Safe may create a false sense of security and lead to complacency. Organisations that have implemented MFA have also experienced security breaches:
- Data was exfiltrated from a networking solution provider as an employee accepted an MFA notification
- A financial solutions provider was hacked and digital gold was transferred by disabling the OTP verification system
Ensuring that MFA delivers the results we expect requires understanding how it can be bypassed, from which we can adopt measures to mitigate its risks.
What Constitutes MFA?
MFA is the use of more than one credential to authenticate a user or provide access to digital assets. The multiple factors in MFA can include
- Something You Know – Passwords/PINs fall under this category
- Weakness – They can be guessed, stolen using malware or through phishing
- Something You Have – The One-time Password (OTP) falls under this category; the user needs to have a device, such as a mobile phone, to receive the OTP
- Weakness – The device can be stolen, or the OTP can be stolen through phishing
- Something You Are – Biometrics, such as fingerprints, establish the user’s identity
- Weakness – Biometrics can be cloned to defeat biometric authentication
- Something You Do – Behavioural attributes that are unique to the individual and the tasks they routinely perform, such as accessing specific files at a specific time in a specific order
- Weakness – Unreliable, as behaviour can vary with context
- Somewhere You Are – The user’s location
- Weakness – Location services like GPS can be spoofed. May not prevent insider attacks
Something You Know (password/PIN) and Something You Have (OTP) are the forms of MFA that most users are familiar with as they are widely encountered in both professional and personal use of digital solutions.
When MFA Stops Being MFA
MFA requires all the utilised factors to be secure. If the MFA implementation requires password + OTP and if the organisation does not enforce cyber hygiene through policy and users are known to recycle or share passwords, or if a data breach has occurred where user credentials may have been leaked, then the organisation effectively only has single factor authentication (the OTP) as passwords may have been compromised.
Similarly, the organisation may implement MFA but a user may effectively only have single factor authentication if the device from which they are trying to gain access to a digital asset is also used to receive the MFA token i.e., it is not an out-of-band device e.g., the user is trying to login to their business email from their phone and the SMS OTP used as a second factor is also received on the same phone. This will not be valid MFA as malware on the phone can steal both their password and the OTP.
Security questions that rely on personal information (e.g., name of the high school you attended) are no longer appropriate as an additional authentication factor as such information is easy to find through social media.
How Can MFA Be Bypassed?
It is a reasonable, and understandable, question. If you receive the second factor (through SMS or an authentication app) on your phone, how can a cyberattacker successfully login assuming the phone is an out-of-band device? There are several methods through which this can be achieved:
1. Physical Theft
The most obvious bypass method is to steal the phone. The OTPs/push notifications for the second factor can be accessed if the threat actor has physical access to the device. It should be noted that the phone need not be stolen as only access is required; insider attacks can occur as an employee can have physical access to another employee’s phone without stealing it.
This method of bypassing MFA may not be very common in the real world as threat actors will need to have your password and have physical access your phone, which may be difficult to achieve.
2. Malware
A malicious app on the phone can be used to steal the second factor. This method requires the user to allow sideloading of apps and to install the malicious app, or provide physical access to someone who will perform such actions on their phone. While possible, this is again not a reliable method for a threat actor to use especially if they wish to compromise specific users as it requires the user to perform specific actions that are not under the attacker’s control (but may be possible with phishing).
3. SIM Swap
A cyberattacker can obtain a SIM with the prospective victim’s phone number, which will enable them to receive SMS OTPs. This method is more effective, especially when targeting specific individuals, as publicly available information can be used (or combined with phishing) to defeat KYC measures and obtain the SIM. Twitter CEO Jack Dorsey’s Twitter account was hacked using a SIM swap.
Employees of the mobile service provider may also use their access privileges (e.g., when a phone number is being ported) to participate in the fraudulent activity without making the user suspicious as the user does not expect the SIM to work during porting.
4. Proxy Server
Using a proxy server if far more reliable, from the perspective of a threat actor. In this method, known as a Man-in-the-Middle (MITM) attack, the user believes they are logging into the genuine website/digital service when they are actually connecting to a malicious website hosted on the proxy server that impersonates the genuine website. When the user enters their credentials in the malicious website, the proxy server forwards the credentials to the genuine website. The genuine website then sends an OTP/MFA token to the user’s out-of-band device. The user enters the OTP in the malicious website which then forwards the OTP to the genuine website, allowing the threat actor to access the genuine website. This method also works when authentication apps/MFA push notifications are used.
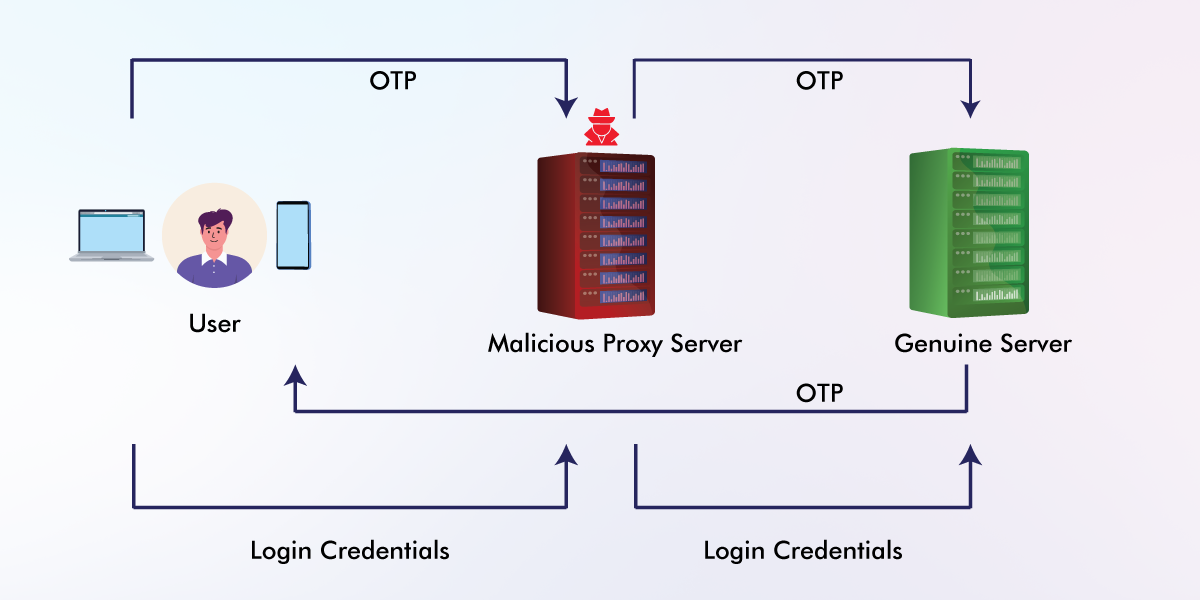
MFA Bypass Using a Malicious Proxy Server
This method requires the user to want to login/approve the MFA notification, which can be achieved through phishing or by sending repeated MFA prompts until the user gives in (MFA bombing/fatigue).
5. Session Cookie Theft
Once MFA is used to authenticate a user, the website/service places a session cookie in the user’s device indicating the user is authenticated to avoid repeated logins. Threat actors can use malware or cross-site scripting to steal the session cookie and access the user’s account as an authenticated user, bypassing MFA.
Should Enterprises Use MFA?
If there are this many (and more) ways to bypass MFA, should enterprises implement MFA? Yes. There are two reasons why enterprises must implement MFA:
- MFA significantly enhances user account protection but, like any technology, has weaknesses. Instead of avoiding MFA, organisations should choose the method of MFA that works best for them, understand how such MFA can be bypassed, and implement mitigation measures to prevent MFA bypass
- If MFA is avoided, threat actors may compromise the organisation and enrol their own devices to receive MFA tokens using the MFA functionality built into many enterprise solutions. This will make it harder for an organisation to regain control of user accounts
Strengthening MFA to Avoid Bypass
Enterprises can adopt several measures to defeat MFA bypass attempts. Consult your cybersecurity partner to identify the method(s) that work best for your organisation and with your MFA architecture.
1. Password Hygiene
We previously discussed that MFA turns into single factor authentication if the password is compromised. The enterprise must stipulate and enforce standards for password length and complexity to avoid passwords being compromised through guessing or brute force attacks. Password sharing and recycling must be prohibited. K7 ISAP can be used to monitor the dark web for credential leaks.
2. Insider Attack Mitigation
Insider attacks, from rogue employees, can be difficult to detect as employees have legitimate access to digital assets and therefore receive legitimate MFA tokens. Enterprises can deploy solutions like K7 InfiniShield that include User and Entity Behaviour Analytics (UEBA) to spot deviations from expected behaviour.
A Maker-Checker process can also be implemented to ensure that potentially destructive actions cannot be initiated by an individual employee and require confirmation/authorisation from another employee. Access to digital assets should be provided following the principle of least privilege and immediate revocation of access (including receipt of MFA tokens) should be included in employee exit procedures.
Web applications should clear a user’s cache when logging out to prevent using a browser back button to access a logged in user’s account. Session IDs should not be sequential or easily guessable to prevent a logged in user from switching to another user’s session. Such vulnerabilities can be identified by using K7’s VAPT services.
3. Mobile Device Protection
Mobile phones are often used as the out-of-band device to deliver the MFA token, through an SMS OTP or an authentication app. Malware and device theft can compromise the MFA token. The mobile device should be protected through a security solution, such as K7 Mobile Security, that can identify and block malware, block phishing websites, remotely lock the device if it is stolen, assist in tracking and retrieving the stolen device, and remotely wiping the device if it cannot be retrieved.
4. Enterprise Device Protection
Malware on a server or employee’s computer can steal MFA tokens or avoid MFA entirely by stealing session cookies. Phishing links may also direct the user to a malicious proxy server instead of a genuine website. Endpoint security solutions such as K7 Endpoint Security use AI-enhanced multi-layered protection to identify and stop all malware in real time, and block phishing links. Such solutions also protect devices against hacking which prevents threat actors from disabling MFA verification systems.
5. SIM Swap Prevention
The ability of SIM cards to be swapped is an MFA vulnerability that is well known to both adversaries and defenders. While some mitigation measures are possible, such as locking the SIM with a PIN or using UEBA to identify malicious activity if the SIM is successfully swapped and MFA tokens compromised, the most effective measure is to avoid using SMS-based OTPs as MFA tokens, and instead use an authenticator app on the phone to deliver the MFA token.
6. Proxy Server Blocking
Protecting against malicious proxy servers (and other MITM attacks) can be challenging as the digital asset being accessed may use a custom domain name that is beyond the ambit of phishing protection. The most effective form of protection, which is also effective against the other MFA bypass techniques discussed here, is implementation of WebAuthn-based authentication that is often deployed through a FIDO2 security key (other deployment methods are available).
WebAuthn prevents MITM attacks as the credentials are bound to a specific URL/service and will therefore not be supplied to a proxy server. This method does not use session cookies which, therefore, cannot be stolen. Hardware security keys are also resistant to malware; they require proximity to the authenticating device for authentication to succeed, and therefore cannot be defeated by stealing the hardware key; and additional biometric verification prevents compromise even if theft + proximity is achieved.
7. Avoiding MFA Fatigue/Bombing
An MFA fatigue/MFA bombing attack tries to flood the user with MFA prompts (e.g., by repeatedly triggering password reset requests) hoping a frustrated or panicked user will accept one of the prompts. Such attacks can be prevented by limiting the number of MFA prompts that can be sent within a time period. Similarly, the number of login attempts within a time period must also be limited.
8. Avoiding User Manipulation
Cyberattackers can contact employees pretending to be enterprise IT support and ask them to share their MFA tokens. Such instances of phishing or social engineering cannot be prevented purely by technology solutions as they rely on persuasion rather than malware and the employee may be contacted through a personal device or social media channel which lie beyond the protection of enterprise cybersecurity solutions. Users must be trained to identify MFA bypass attempts and phishing to prevent such attacks from succeeding.
Users must also be made aware of the dangers of sharing information on social media, especially without privacy safeguards, to avoid identity theft.
Precautions in MFA Bypass Mitigation
We have examined 5 types of factors used in MFA (something you know, have, are, do, and somewhere you are) and noted that only two factors are usually used. Other factors, however, can be used if the two factors are cleared but there is reason to be suspicious. E.g., the MFA implementation requires a password + OTP from an authenticator app. Both were cleared but an incorrect password was entered multiple times before the correct password was used. A third factor can now be introduced, such as asking for a biometric input, to authenticate the user.
It should be noted that the third/fallback factor should not be less secure than the primary factors used for authentication i.e., an SMS OTP (which is vulnerable to SIM swapping and phishing) should not be used as a third factor if there is reason to believe the OTP from the authenticator app has been compromised.
Multi-Factor Authentication can prevent over 99.9% of account compromise attacks, but its implementation determines its effectiveness. Contact Us to learn more about how K7 can help you gain robust MFA and secure your enterprise against both external and internal attacks.











