This blog is a snapshot of our K7 Cyber Threat Monitor Report for Q1, 2022–23. Get your copy right now!
The first quarter of 2022-23 was notable in the industrial threat landscape. While MSMEs and large enterprises enjoy the virtues of connected devices and growing automation processes, threat actors are increasing their efforts with more sophisticated attack techniques leveraging finicky targets. The online availability of unpatched vulnerabilities, unsecured credentials, weak configurations, and outdated industrial protocols makes the job easy. However, while in operation, threat actors are rerouting their attacks and operating remotely as a more smart yet cunning gesture. The individuals aren’t safe either. The ease and acceptability of digital transactions have made each a potential victim.
Amid the ongoing chaos, we at K7 Computing have rolled out our latest Cyber Threat Monitor report, highlighting our findings from Q1, 2022–23.
The K7 CTM report garners insight from overseeing hundreds of thousands of attacks. With our several decades of hold over the cybersecurity space, most of them have been thwarted. However, that doesn’t decrease their peril and ability to hunt down other victims.
Let’s look at the most significant data points from the quarterly K7 Cyber Threat Monitor Report: Q1, 2022–23:
The Infection Rate soared up by a whopping 7%
The ongoing hybrid war between Russia and Ukraine is an alarming example of how the future threat landscape could be shaped. The war is an example of how a battle is fought with guns and artillery alongside cyberspace. Both sides display the effects of hacktivism by executing a series of malware to destroy their enemies and a plethora of computers and information. Russia used wiper malware in Ukraine months before the actual conflict began.
The example is not of a single person but of how future wars between nations could play out. In these future wars, threat actors would play a more significant role than the state’s defense by harming the enemy nation by catapulting malware, DDOS attacks, phishing, and ransomware, resulting in financial and informational destruction.
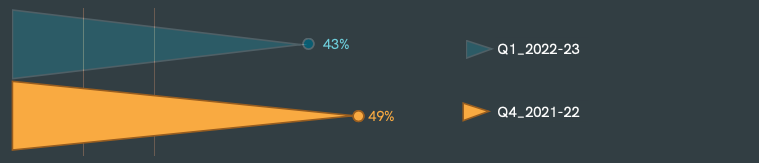
Adding the activities of the nation-state actors with the malicious groups and individual threat actors, you can see how the attacks are compounding at an astounding level every financial quarter. In Q1, 2022-23, we noticed the countrywide Infection rates soar. The chart mentioned above is a piece of evidence showcasing the gross picture.
Smartphones- the colossal attack vector
The perpetual growth of smartphones is not restricted to individuals anymore. Employees of both large enterprises and MSMEs are increasingly using smartphones as an alternative device to retrieve business and financial information. And this is the primary reason threat actors see handheld devices as a catalyst to launch large-scale targeted attacks.
Phishing has become a core attack vector for executing ransomware and other colossal attacks on enterprises. As a result, threat actors have adapted to strengthening their armor and have become more innovative and sophisticated in multifold targeted attacks. The comparison graph below displays how the threat actors focus more on developing Trojans masquerading as legitimate-looking apps to heighten their menace.
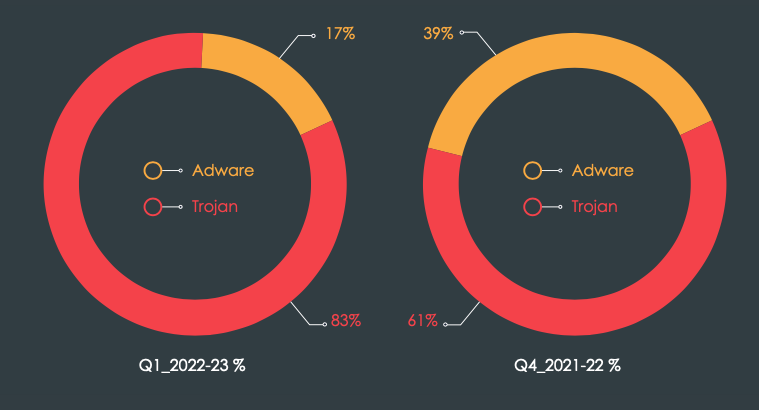
Adware vs. Trojan proportional split
In many of our previous editions of the CTM report, we have rung the caution bell on how fake apps are doing the rounds on Google’s Play Store and other third-party websites.
The swelling numbers of downloaders and agent malware
In Q1, 2022–23, we observed a large variety of dropper and downloader malware occupying a significant chunk of the threat landscape. Across platforms, threat actors used droppers in multi-stage attacks where additional malicious payloads are downloaded or dropped via a remotely held command-and-control (C2) server via backdoors later used for various nefarious purposes.
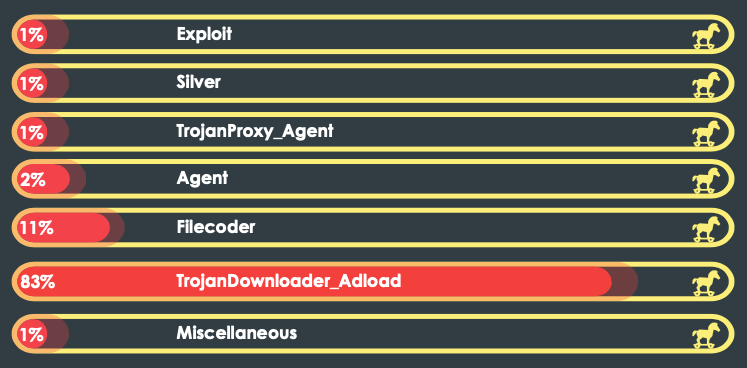
Trojan detection trend lines of macOS, Q1, 2022-23
The burgeoning proportion of Adload in the macOS space illustrates the growing dependence on downloader malware. In the Windows section, too, the presence of Adw.Win32.Setupdownloader is especially noticeable since its existence has increased trifold compared with the previous quarter.
Download the K7 Q4 2021-22 Cyber Threat Monitor report!
Additional Resources
- Experience K7 Enterprise Endpoint Security now
- Get in touch with K7 Computing experts for any customized cybersecurity-related services < 18004190077 | businessenquiry@k7computing.com
- Know more about K7 Enterprise Endpoint Security











